I want to bring this up to HostGator, but want to verify my suspicions before making a big fuss.
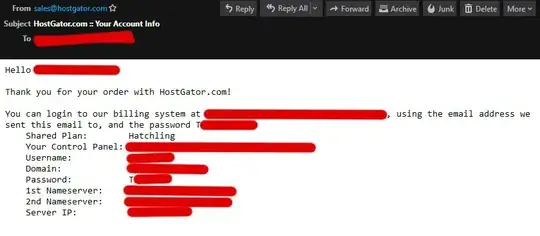
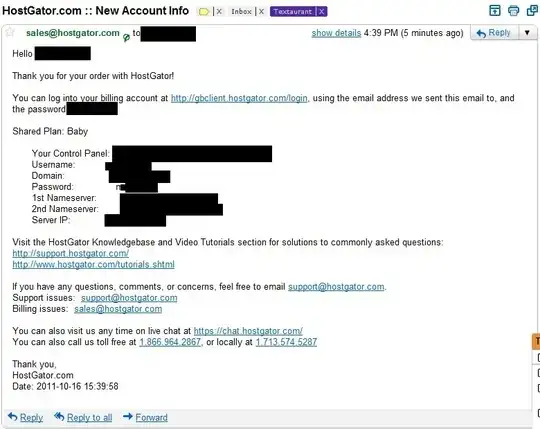
I asked a customer care representative to help me add an SSL certificate to a site I host with them. When he was done, I received this e-mail with all my login information, and my entire password in plain text (I left the first letter visible as evidence). I set up this password over a year ago, and it was a big surprise to find out they sent it back to me, unprompted, in plaintext:
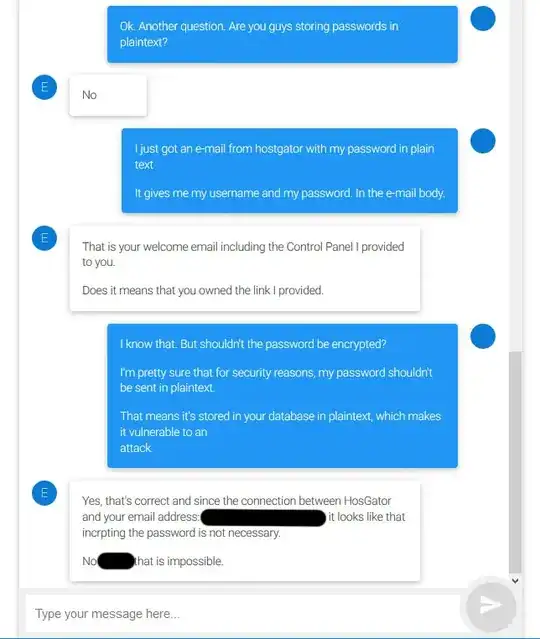
I immediately brought this up to the representative, who repeatedly tried to convince me that it was OK. I decided to drop it after a few minutes, because I think I should bring it up to someone higher up. Before I do so, is it safe to assume that my password is stored in their database as plain text? If so, do you have any suggestions on how to address this issue with the provider?