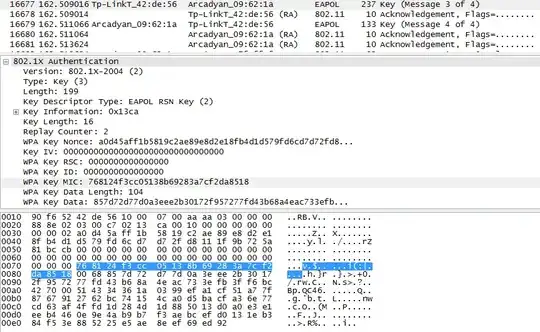
WPA2 has three main key types:
- Pairwise Master Key (PMK) - the shared passphrase
- Pairwise Transient Key (PTK) - a key used for securing communications with individual clients
- Group Temporal Key (GTK) - a key used for securing multicast traffic
The PTK is generated from the following data:
- Shared passphrase (PMK)
- A nonce value generated by the access point (ANonce)
- A nonce value generated by the client station (SNonce)
- Access point MAC address
- Client station MAC address
The SNonce value has its authenticity and integrity provided by a Message Integrity Code (MIC). Strictly speaking this should be called the MAIC, because it provides authenticity as well as integrity.
The above values (excluding the MIC) are concatenated and put through PBKDF2-SHA1, in order to generate the PTK. After this, the AP sends the GTK (and a corresponding MIC) to the client. The PTK and GTK are then used as the encryption keys for further transmissions, for unicast and multicast respectively.
The overall handshake looks like this:
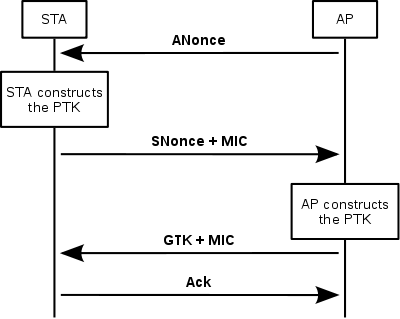
If the attacker captures the PTK, ANonce, SNonce, AP MAC and client MAC values via network sniffing, he can then brute-force the PMK. The MICs do not need to be known, because they does not contribute the PTK value.
Since PBKDF2 is a slow key derivation algorithm, a normal bruteforce would be rather inefficient. A dictionary attack is much more feasible.
Further reading: