The wpa2 mic is a 16 bytes array which is built by Hmac(sha1) ,But the Hmac(sha1) returns 20 bytes array. So where does that 4 bytes go?
-
3I'm not sure what you're asking. Why can't HMAC-SHA1 return 16 bytes if you truncate? – forest Feb 26 '19 at 08:30
-
Yes we can truncate it but I need all the bytes of the hash to decrypt it! – msx Feb 26 '19 at 10:00
-
1@msx forest is right, they actually get truncated. – Azteca Feb 26 '19 at 22:34
1 Answers
It's supposed to be "negotiated" but the size of MIC is fixed to 16 octets, so independently from the algorithm used eventually it'll be truncated.
11.6.3 EAPOL-Key frame construction and processing
[...] EAPOL-Key frames are constructed and processed according to the AKM negotiated at association time. The negotiated AKM determines what algorithm is used to construct and verify a MIC, the size of the MIC, and the algorithm used to wrap and unwrap the Key Data field.
Table 11-9 - Integrity and key-wrap algorithms
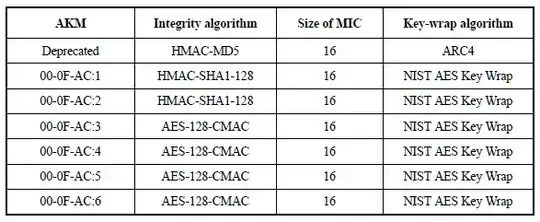
So, they're discarded:
11.6.2 EAPOL-Key frames
HMAC-SHA1-128 is the EAPOL-Key MIC. HMAC is defined in IETF RFC 2104; and SHA1, by FIPS PUB 180-3-2008. The output of the HMAC-SHA1 shall be truncated to its 128 MSBs (octets 0–15 of the digest output by HMAC-SHA1), i.e., the last four octets generated shall be discarded.
Taken from:
Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications. (IEEE Std 802.11 - 2012)
- 1,116
- 7
- 16