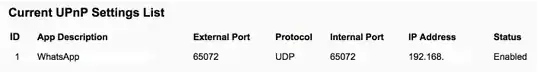
I have logged in into my router using the web interface. I was checking UPnP forwarding (which is enabled by default), and found out that whatsapp is initiating a UPnP request on port 65072. Is there a way that I can understand, why and how whatsapp is using UPnP? Is it something normal ?
Found an application (Whatsapp) initiating UPnP requests, is it something that I should worry about?
-
1Lots of apps do this to allow peer-to-peer communication – paj28 Jan 10 '19 at 09:01
-
Can you reproduce this log again by calling someone on your WhatsApp? It's not supposed to use uPnP. WhatsApp uses **STUN** for establishing **VOIP**. – defalt Jan 11 '19 at 13:09
-
I was just fiddling with my router's UPnP setting up a Plex server and found WhatsApp there. I deactivated/reactivated UPnP and it went away, I regret not having done a screenshot. Will keep an eye on it and report back. – brasofilo Jan 12 '19 at 00:56
-
1I scanned many pages of Google results and the *only* mention I found to this issue is from 2017 on this SuperUser question (no answers): [Are applications able to open ports in modem without permission?](https://superuser.com/q/1251233/138315) – brasofilo Jan 12 '19 at 01:40
-
@defalt, actually it is reproduced when I call someone. – Hadev Jan 12 '19 at 05:19
-
@brasofilo, I think if you make a call using Whatsapp you will get Whatsapp under your UpnP setting list. I think that's the reason of Whatsapp showing up there, but why and how, I 'm still not sure if it's a normal behavior or not – Hadev Jan 12 '19 at 05:25
-
It's probably using uPnP for external IP Address discovery and dynamic port forwarding. The normal behaviour would be to use STUN protocol to set up VOIP. These are NAT traversal techniques. They might have add uPnP in their latter updates. Good finding. I'll look into this and update this as answer. – defalt Jan 12 '19 at 05:52
-
Yes indeed, I made a WhatsApp call from one mobile to another and both appeared under UPnP listing. And they disappear after finishing the call. – brasofilo Jan 12 '19 at 13:06
2 Answers
WhatsApp uses uPnP for NAT traversal and external IP Address discovery. It only happens when you initialise WhatsApp call.
Some of the NAT traversal techniques are:
- NAT-PMP (obsolete but still used by some of the BitTorrent clients)
- PCP (successor of NAT-PMP)
- STUN/TURN
- uPnP (also used by BitTorrent client)
Through uPnP WhatsApp establishes peer-to-peer communication to initiate VoIP. uPnP is also a dynamic port forwarding technique so it is active as long as the P2P communication is running. If you disable uPnP in your router, then WhatsApp switches to STUN.
It used to be only STUN/TURN in older versions and they recently added uPnP support. I think it is because they want to reduce the call set up time. STUN has its own complications like it doesn't work with Symmetric NAT and first client has to discover if it is sitting behind a Symmetric NAT, then only it switches to TURN using ICE which further increases call set up time.
Whereas in uPnP, client only has to talk to the router to initialise the session and keep it active. This greatly reduces the round trips and call set up time.
WhatsApp itself is owned by Facebook and is an end to end encrypted communication service. As a communication protocol, it has many features and functions which people use to communicate including voice and chat. On its own, WhatsApp is not a bad service and is used by millions of users around the globe.
If you are not familiar with the application and are sure none of the users within your home are leveraging it, I would recommend identifying the internal source and removing it. WhatsApp is a communication service which could be used to send bot commands or retrieve data from a potential zombie within your network.
- 1,421
- 5
- 12
-
Can you please elaborate more on how can that be used to retrieve data from users within the network? – Hadev Jan 12 '19 at 05:20
-
1Say I create a bot for WhatsApp and I install it on your machine. I could theoretically start feeding data files, network traffic, passwords, etc. through the bot to a remote account without making you aware that it has occurred. I don't know for sure that this particular path has been leveraged, but the use of IRC for such an attack is well documented. – Connor Peoples Jan 12 '19 at 06:51