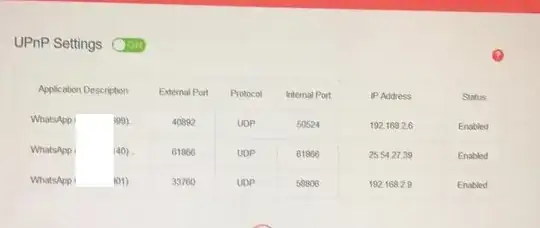
When available, WhatsApp uses uPnP for dynamic port forwarding and external IP address discovery to establish peer-to-peer VoIP session. The external IP address you are seeing is the public IP address of someone with whom you are on call via WhatsApp. If it is not you, then someone in your family is making a VoIP. uPnP settings only shows active uPnP connections.
uPnP is the NAT traversal protocol which opens a temporary port for inbound traffic and forwards it to the uPnP client (like WhatsApp and BitTorrent client). NAT by default blocks any inbound traffic to whom you didn't send the request first. A uPnP client makes a request to uPnP listener which is your wifi router to punch a hole in NAT which allows anyone to reach out to the uPnP client. This allows the caller to send you session data without getting blocked by NAT.
Another purpose of uPnP is to let apps using peer-to-peer protocol to discover your external IP address in order to advertise how others can reach out to you without getting blocked by NAT. In VoIP, this advertising is called signalling. Signalling is not a part of uPnP.
Another method that WhatsApp uses for NAT traversal is STUN protocol which achieves the same purpose but that won't show up in your router logs.
You should ask your WhatsApp contact why he/she is using the internet of UK Ministry of Defense. They could be under surveillance.
You can read some more details in this answer: Found an application (Whatsapp) initiating UPnP requests, is it something that I should worry about?