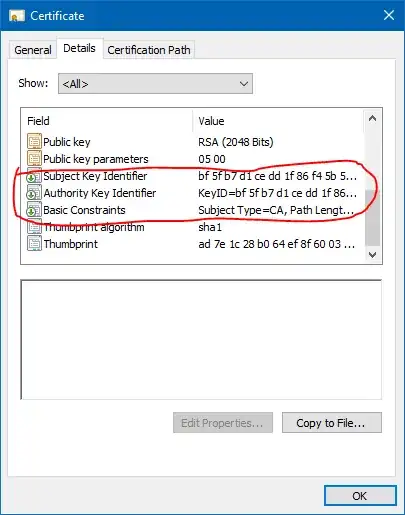
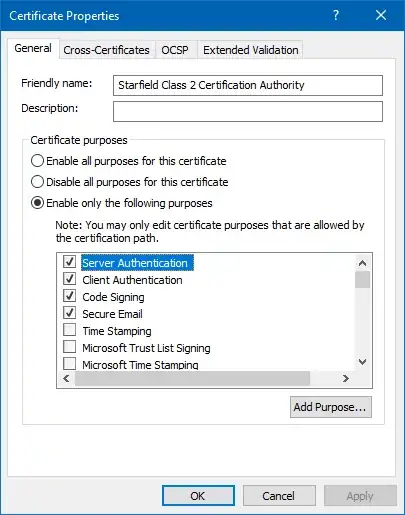
I recently started using AWS's Certificate Manager to get free TLS certificates for my load balancer. When I was inspecting the certificate chain I noticed that the Root CA, Starfield Class 2 Certification Authority, has the following extended key usage values:
- SSL client
- SSL server
- Netscape SSL server
- S/MIME signing
- S/MIME encryption
- CRL signing
- Any Purpose
- OCSP helper
- Time Stamp signing
I then opened up the Trusted Root Certification Authorities store on a Windows laptop I have and started looking at several of the root CAs. It turns out that a lot of them have the same or very similar EKU values. I understand why CRL and OCSP are present (even though I would imagine the root would be kept offline which would make OCSP a bit more difficult), but why the others? Does this mean that the CA, in addition to issuing certificates, can also sign code, perform S/MIME functionality, etc.? Or does the presence of these values mean that certificates that descend from this root CA can only be used for, at most, those EKU values?
I briefly skimmed the Extended Key Usage section of RFC 5280 and the only thing I saw on the topic was this:
In general, this extension will appear only in end entity certificates.
To summarize my questions:
- Does placing these EKU values in the root CA cert indicate that the end-entity certificates descending from that root can have, at most, those EKU values?
- If no to 1, why are these values present in multiple root CAs? Is it so these CAs can also be used for those purposes? If so, why would one want to do that instead of issuing an end-entity certificate with those EKUs?