I'm trying to find a basis for comparing key pair based authentication with password based authentication, and their relative resistance to guessing / brute force attacks.
I appreciate that a user-chosen password will likely have a lot less entropy than a random one - has there been any attempt to measure the difference?
For a brute force attack, I expect the cost of generating a key pair will be much higher than for generating a password, but is there much of a difference in the cost for validating the key pair compared with validating a password?
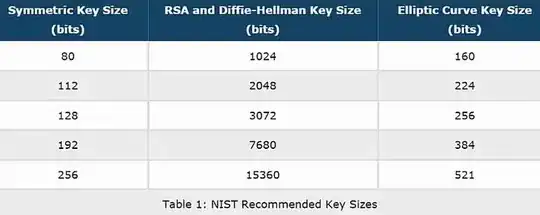
A password of a given length could potentially be any string of characters of that length, so a simple incrementing counter converted to a string of character codes would give every possible password. However the same does not apply to a key pair - indeed the number of possible values appears to be very sparse. Are there any estimates of how many key pairs exist for a given algorithm / key size?