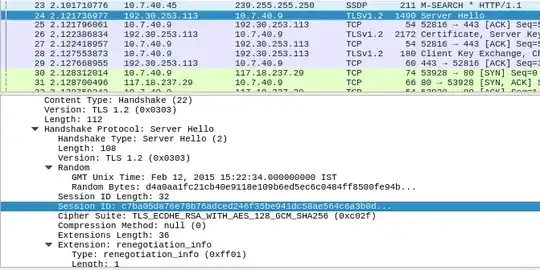
I was trying to understand the TLS handshake in depth. I set up Wireshark and captured the github.com traffic. While inspecting the Client Hello and Server Hello, I found a parameter Session ID.
According to this article session id can be used in case we want to reconnect without a big handshake. What I understand is, if we had previously connected, then the cached session id can be used again for the latest session. In that case, we are sending the session id as plain text. Can this be captured by an attacker?
Or, am I completely wrong here? Is this different from the symmetric key?