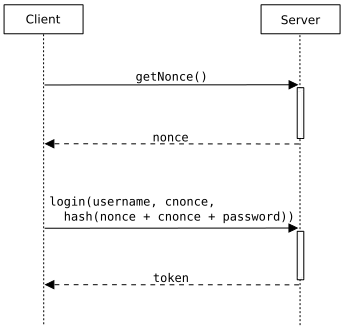
As we all know, nonce is needed to prevent replay attacks. Everywhere I read about nonce, I see that client always fetches one from the server, and, to improve security even more, it also can add its own client nonce (cnonce).
Just like on this diagram:
This scheme adds an overhead of one more roundtrip to the server; and I'm trying to figure which attack vectors will become possible if we only use client nonce, and ensure on the server that cnonces are never reused (to avoid storing all used cnonces, obviously we could just require that every next cnonce for a given API key is larger than the previous one, and only store the last cnonce for the given API key).
So far I fail to find any new attack vector: by ensuring that cnonces can never be reused for each API key, we eliminate replay attacks completely. Am I missing something?