I am using WinHTTP on a Delphi project to make calls over to the server.
Script:
userAgent := 'TestClient.exe';
hsession := WinHttpOpen(pwidechar(userAgent), WINHTTP_ACCESS_TYPE_DEFAULT_PROXY, nil, nil, 0);
if(hsession = nil) then ShowMessage('Failed WinhttpOpen');
p := 'https';
port := 443;
requestflags := WINHTTP_FLAG_SECURE;
server := '10.0.0.221';
hconnection := WinHttpConnect(hsession, PWideChar(server), port, 0);
if(hconnection = nil) then
begin
le := GetLastError;
ShowMessage('Failed to connect: ' + IntToStr(le));
end;
Action := 'GET';
hInetRequest := WinHttpOpenRequest(hconnection, pwidechar(Action), nil, nil, nil, nil, WINHTTP_FLAG_SECURE);
if(hInetRequest = nil) then
begin
le := GetLastError;
ShowMessage('Failed to connect: ' + IntToStr(le));
end;
WinResult:=WinHttpSendRequest(hInetRequest, nil,0, 0, 0,0,0);
if(not WinResult) then
begin
le := GetLastError;
WinHttpCloseHandle(hInetRequest);
ShowMessage('No result obtained : ' + IntToStr(le));
end;
Question; For security compliance (FIA_X509_EXT1.1), should connection terminate right after SSL handshake? In case peer certificate is deemed invalid. Or is this ok to terminate later?
Actual: What's happening, is that the client (using WinHTTP) makes a call and successfully confirms the TLS handshake, even when the certificate is invalid. However, right after handshake and before completing request, it terminates the connection throwing a '12175' error. Which is the error for invalid certificates? Which is right?
Problem: For above (FIA_X509_EXT1.1) compliance to pass as per verification tool, WinHTTP must not allow successful handshake, and hence terminate the connection earlier.
Wireshark screen attached below: (10.0.0.221 is the server)
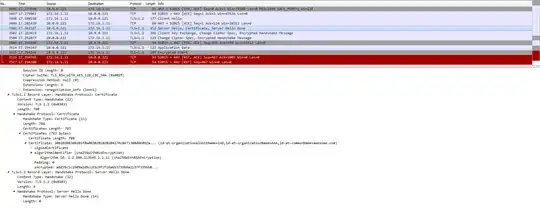
I already asked this question in stack exchange, but as suggested by another member, this is probably the right place.