From the official FAQ on the vulnerability (emphasis mine):
So again, update all your devices once security updates are available. Finally, although an unpatched client can still connect to a patched AP, and vice versa, both the client and AP must be patched to defend against all attacks!
Does this mean that a subset of the collection of attacks discovered can be prevented even if only 1 end of the connection has been repaired?
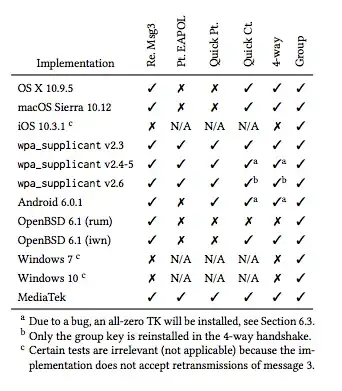
This image from Arstechnica, apparently a screen capture from the initial presentation, shows various platform implementations being subject to different KRACK attacks. This implies that at least part of the problem can be fixed from only the client side.
It's not clear what, or how much, client side only fixes can address. Do these represent 6 different ways to do the same attack? 6 different ways to tamper with a compromised connection? Something else? A combination of the previous?