The head of our IT department and Networking class in my college has given me and another student a challenge; he told us that if we could clone the NFC tags in our student ID's used to sign in on time, he would give one of us unlimited access to the colour printers for a year. His main motto that he always talks about though is encouraging students to learn through experimentation regardless of whether the students ideas will work or not. He wants us to experience failure as well as success through our own attempts.
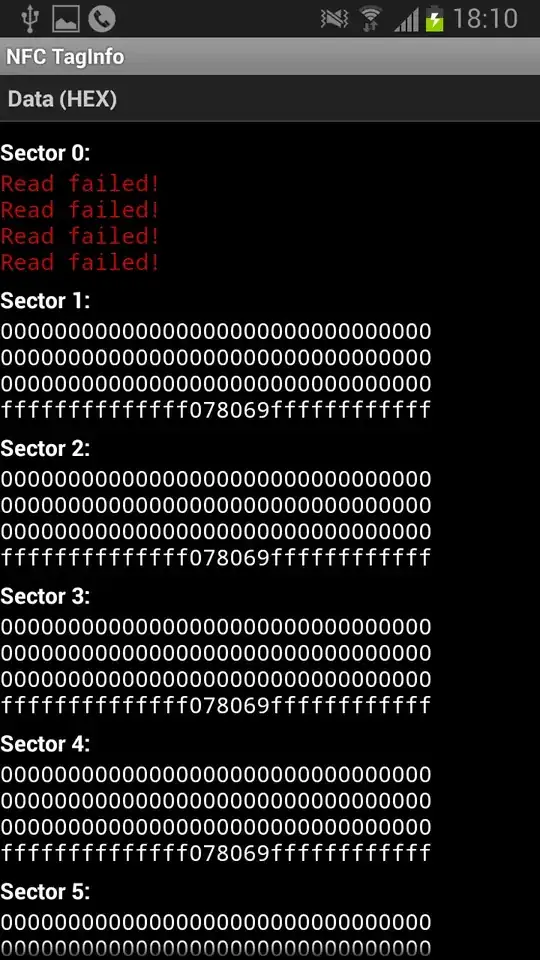
I'm a bit skeptical as to whether it will work because I've read forums online that say this a futile attempt because no reputable academic institution or business would leave their NFC tags unprotected and completely vulnerable to complete cloning.
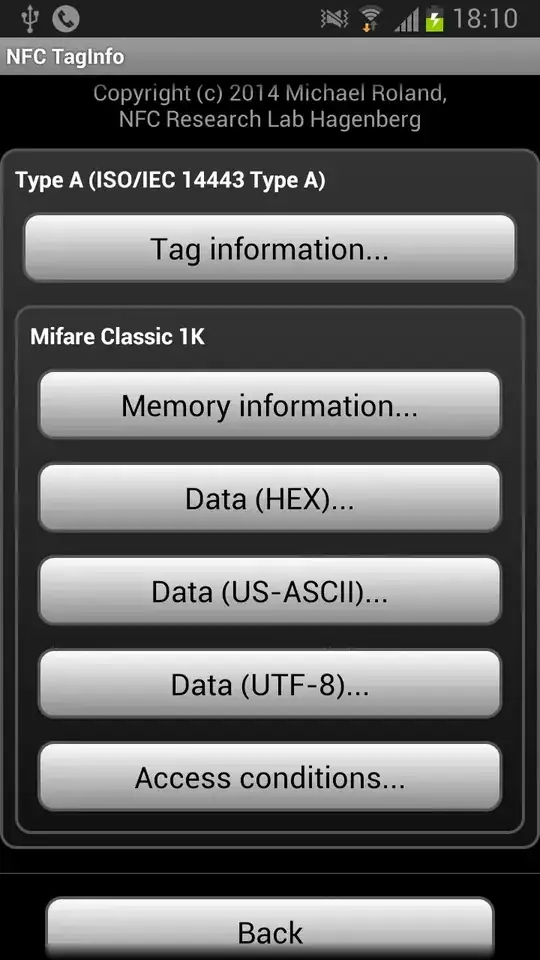
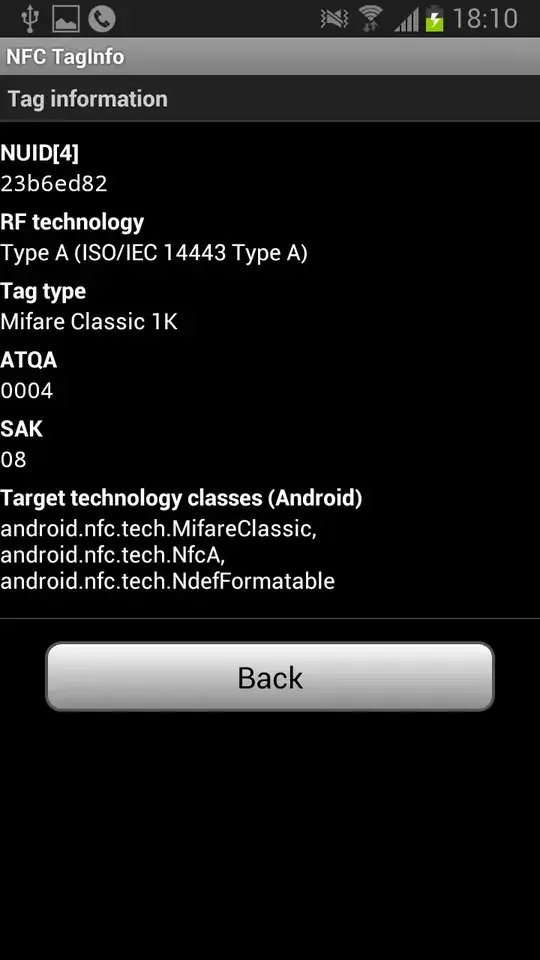
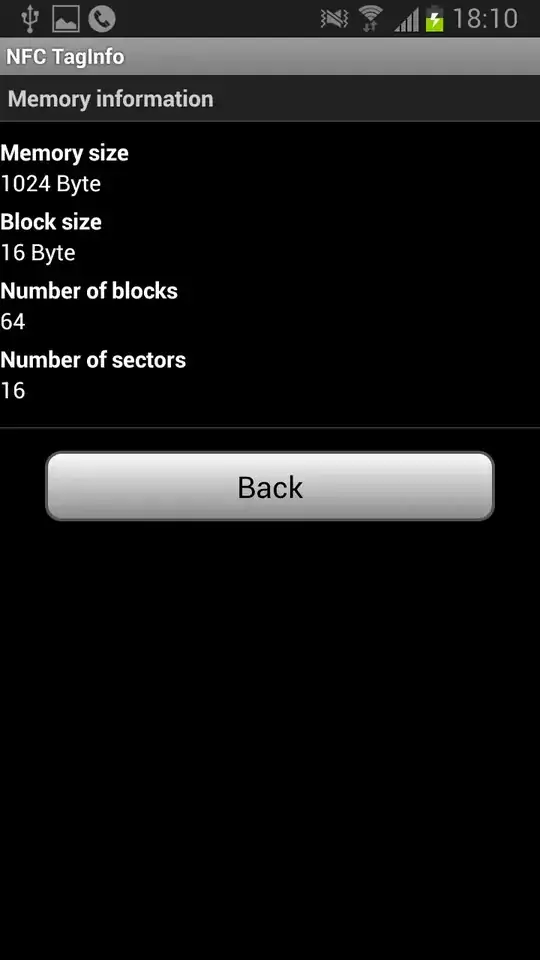
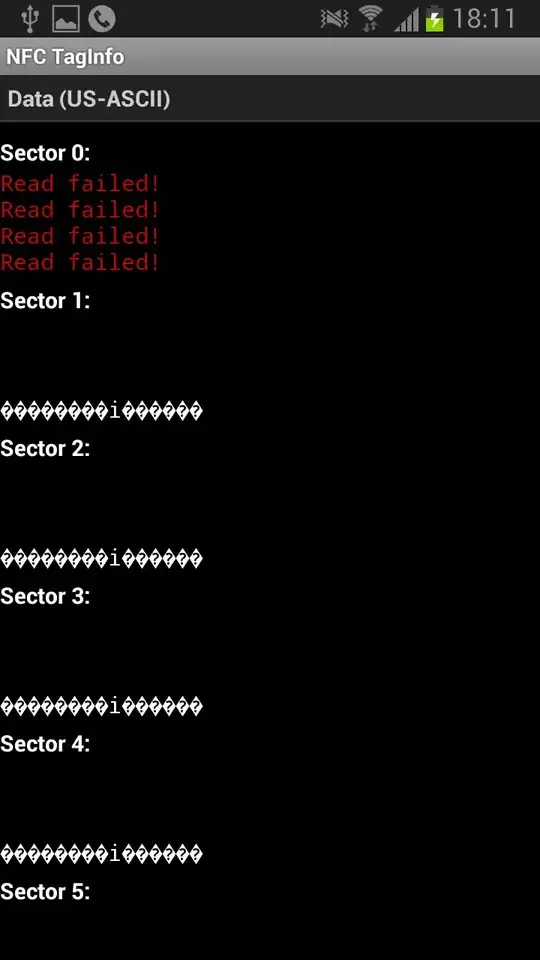
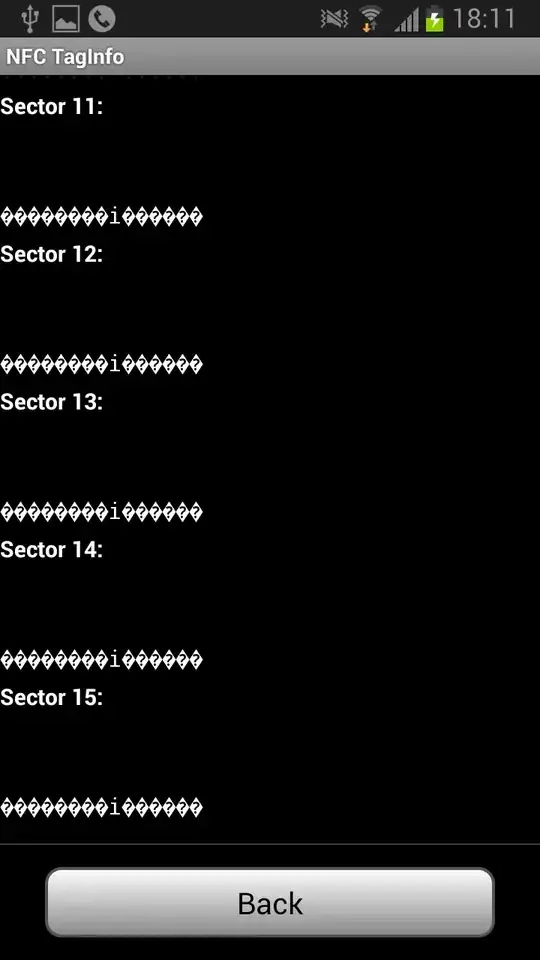
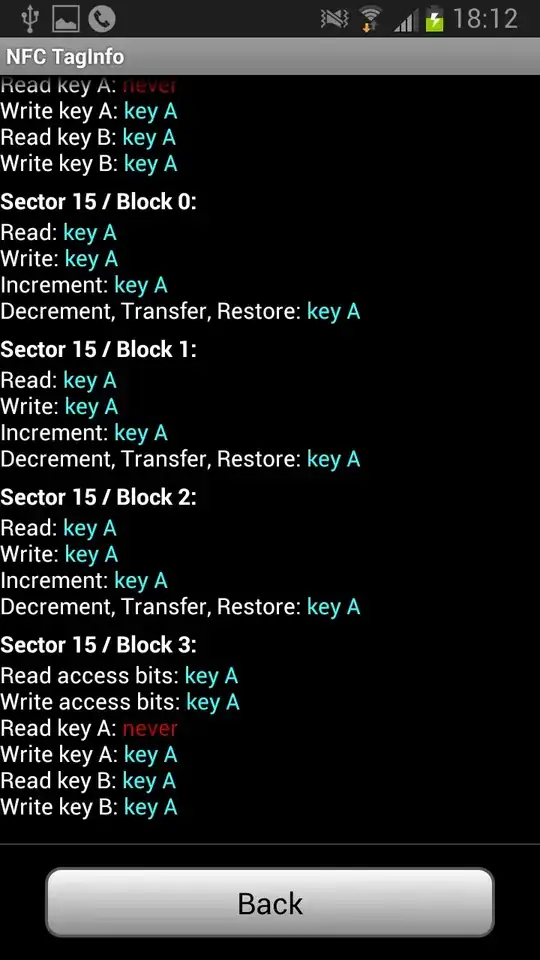
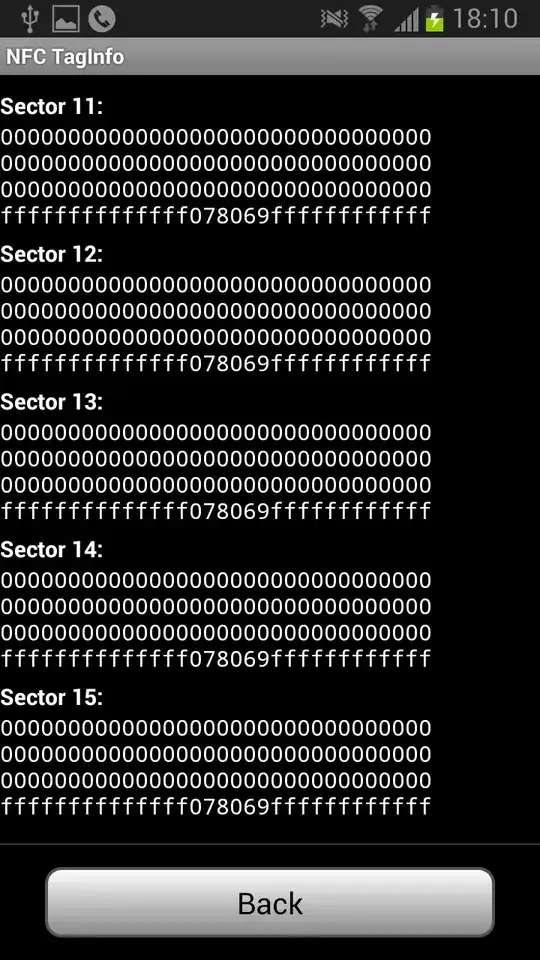
From scanning the card with my Android phone, I see that it uses a Mifare Classic 1k tag.
Does anyone have an idea how to replicate it? There are some cheap tags on eBay but I wonder if I should bother if it's not even possible to clone it.