Are those the total steps? An image would really help.
The process you detail isn't quite accurate. For one, WPA2-Enterprise doesn't make use of a PSK. Pre-shared keys are used by WPA2-Personal.
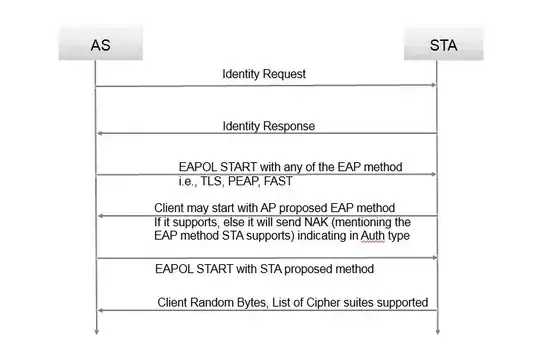
WPA2-Enterprise uses 802.1X to authenticate an device to the network. The protocol used by 802.1X is EAP (extensible authentication protocol) which is defined in RFC 3748.
EAP allows for a variety of different methods to authenticate; you reference EAP-TLS as an example which is defined by RFC 5216. Each EAP method is responsible for describing in their specification how the MSK is created. So the actual process can vary depending on the method used. You would have to reference the specification for each method you are interested in to determine exactly what is taking place.
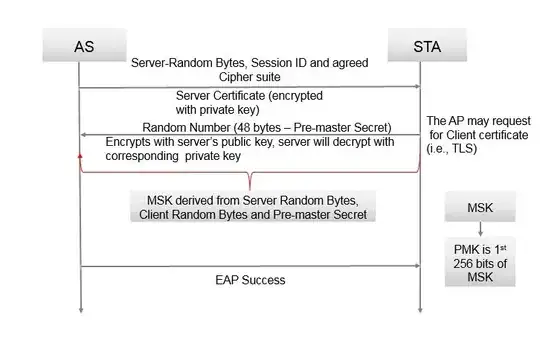
No matter what process is used to create the MSK, this is provided to both the supplicant and the NAS during the EAP transaction and is the basis for the PMK used by 802.11.
In case both sides are using certificates (EAP-TLS) then how exactly is the PMK generated? There is no PSK with certificates.
I know I said it already, but there is no PSK involved. The PMK is generated from the EAP MSK and again the exact method of generating the MSK would be determined by the EAP method. Specifically, the PMK is the first 32 bytes of the MSK.
I read on a security website that: "The weakness in the WPA2-PSK system is that the encrypted password is shared in what is known as the 4-way handshake". But in other websites I read that neither the PMK nor the PTK are ever sent during the handshake. So which is it?
Neither the PMK, the PTK or the PSK is sent during the handshake. However, when you are using a PSK, the PSK is used to generate the PTK so any device that knows the PSK and captures the handshake can then also generate the PTK used and decrypt all the traffic.
With WPA2-Enterprise, the MSK for each EAP transaction should be "unique" to that exchange, so the PMK will be different each time a device connects and authenticates to the network. No other device has access to the MSK/PMK and as such even when the handshake is captured, they will not be able to realistically generate the PTK used or decrypt the traffic.