Could someone explain something to me please:
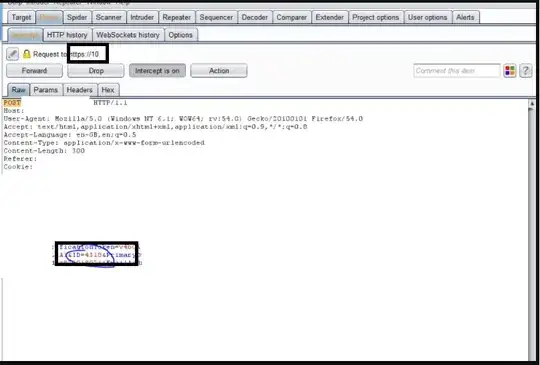
I am intercepting requests on my local proxy to a HTTPS server. The POST body has data such as "ID=4001" in plain text when I intercept it. Firstly, is this normal? Is the HTTPS in place on this server weak or lackluster somehow?
Can someone explain why what I deem sensitive information would be in plaintext here?
- Did the devs drop the ball and present it in plaintext for the client to easily tamper with?
- Would this be encrypted if the HTTPS was properly configured?
- Because im intercepting requests locally from my own machine, HTTPS has no benefit until the request flies off across the network/transmission?
I am intercepting the requests locally from my client directly (not across the network so to speak). Trying to gain a little clarity on this for my own understanding, am I right in thinking at this stage HTTPS has little to no impact and the ID=4001 is a fault on the developers end?
ps. this ID is very sensitive and we wouldn't want someone knowing it or tampering with it successfully.
Update: I guess my question is, I can see this ID param/value in plaintext in burpsuite when intercepting client packets against a web application running on a self-signed HTTPs cert(I assume self-signed is irrelevant), is the fact I can see this ID a fault on the developers? or am I being silly and this would be encrypted in a real production environment? see image: