After installing Firefox 54.0.1 on my work laptop, the first page I see warns me that "Your connection is not secure" when opening https://www.mozilla.org/.
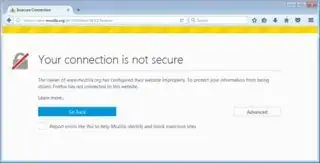
"The owner of Firefox has configured their website improperly"
After browsing a bit more, I noticed that Firefox wasn't just reporting errors for Mozilla.
Firefox is reporting HTTPS security errors for Google, Microsoft, Dropbox, GitHub, Wikipedia, LastPass, Netflix, Facebook, Twitter, Skype, WhatsApp, WolframAlpha, Amazon, LinkedIn, AutoHotkey, Yahoo, Imgur, and even Stack Exchange.
There are a few things worth noting about these errors.
- Neither Google Chrome 59.0.3071.115 or Internet Explorer 10.0.9200.22139 report security issues on any of the listed websites
- A select few sites load in Firefox without reporting any security errors, including Discover, Visa, Mastercard, Chase, American Express, Citibank, Capital One, Bank of America, PayPal, Stripe, Intuit, TreasuryDirect, iCloud*, Discord, and YouTube.
- (Concerningly, a majority of the sites which load without reporting any security errors are related to online banking and finance)
- I am able to load Mozilla's support page and Wells Fargo without security errors, but the pages render as text without any images or formatting
It's worth restating that these security errors are happening on a work-issued laptop, meaning that my employer is most likely scanning HTTPS traffic.
While HTTPS scanning can at least partially explain the HTTPS security errors, the situation still leaves me with a few questions.
- Why is Firefox the only browser reporting these security errors?
- Why isn't Firefox reporting security errors on banking and financial websites?
- Why do some pages not report security errors, but only load as plain text?
*Note: While iCloud did not report any security errors, the page did eventually fail to load with a connection error.