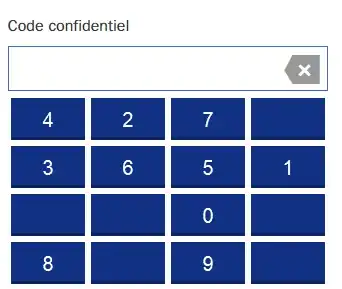
More and more web sites use for an authentication some digits keyboards with random position instead of password. Like this
Could someone explain me the idea of this instead usual login and password?
I have an idea that it seems to be more secure because if you capture traffic of someone you'll get only coordinates clicked and these coordinates are different every time.
But in this case server should transfer the positions of each button to a client to make last be able to display it correctly (4 is top left corner, 8 in bottom left, etc)
If the traffic can be captured so we can capture the position of each digit and coordinates clicked after.
Why is it more stable that common login / password with htts enscrition?