I'm in the process of implementing 802.1x WPA2 Enterprise Authentication using FreeRadius and EAP-TLS (Mutual TLS Cert Based Auth).
I am keen to understand how to actual protocols work together and how they keep our WiFi network safe.
I understand the basics of Cert-based auth, using pub/priv keys. I also know that in regular HTTPS, a session key is created by the client, and sent to the server, however EAP-TLS doesn't seem to work like this.
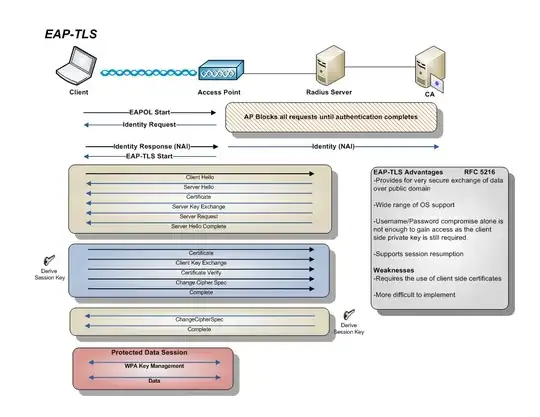
I am looking at this diagram: http://tldp.org/HOWTO/8021X-HOWTO/images/8021X-KeyManagement.png
My understanding (after reading the above diagram) is that after TLS auth is successful, the FreeRadius server will generate a Master Key, and then derive a Pairwise Master Key (PMK). It will then somehow send the PMK to both the Client Supplicant and the Access Point, and then they will use the PMK to generate other session keys to encrypt the actual data.
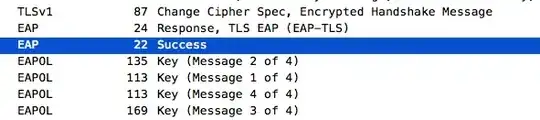
However, after doing some tcpdumps on both my laptop and the FreeRadius server, I do not see any keys being sent or received, apart from the following.... In the capture from the Freeradius server, inside the final Access-Accept packet being sent to the AP, I see MPPE-Send and MPPE-Recv keys, which is weird, as I'm not using MSCHAPv2.....
On the client (laptop) side capture, I do not see anything between the final EAP Success (That is basically empty), and the start of the 4-way WPA2 handshake (at which point the PMK must be known)
So my question is, where is the PMK being sent from FreeRadius to the AP and Client?
Thanks!