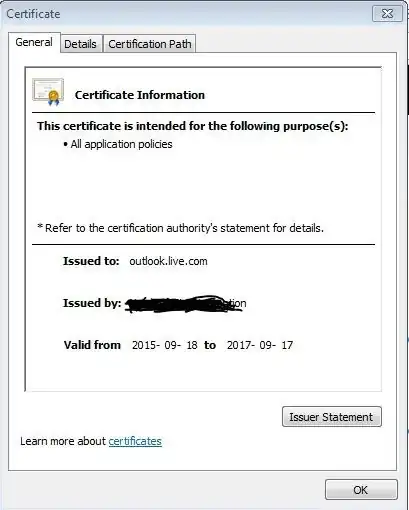
At my company, I get a warning flag that the traffic to the website may not be secure (enough). For instance: outlook.com and gmail.com. When I open the certificate I see this "issued for" and "issued by".
I blackened out the name of my company. Here is the name of "My Company ABC" mentioned, not for instance Gmail or Outlook. This particular message is taken from the web browser warning (either Outlook or Chrome).
For instance, for Gmail, it says:
"SHA-1 Certificate. The certificate for this site expires in 2017 or later, and the certificate chain contains a certificate signed using SHA-1. The connection to this site is encrypted and authenticated using a strong protocol (TLS 1.2), a strong key exchange (ECDHE_RSA with P-256), and a strong cipher (AES_128_GCM)".
It looks to me that the communication from my client to the router is secure and strong, but not stronger than the company has the power to decrypt when needed? While they promise to send it with full encryption from their router that route out to Inter-AS and the endpoint (gmail, outlook..).
Why is it like this and what is the impact? Is this some kind of security trend going around?