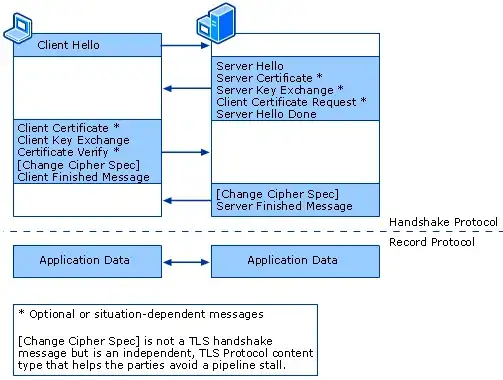
At what stage in below TLS connection setup did the server prove to client that it possesses the private key corresponding to its public RSA key.
I have used TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
Cipher suite to successfully setup a server client mutually authenticated connection. I am just curious how it works. I have a rough idea about Diffie Hellman key generation(I believe it is independent of authentication, and just for generation of secret to create symmetric key) but I could not understand in below sequence diagram, where did the server prove its possession of private key(I know that only private key decrypts what public key encrypts, but any hacker could send a copy of public certificate of any server)