I captured Bluetooth traffic between a master vault Bluetooth smart padlock and an iPhone 6s. This was done using a Bluetooth sniffer and the captured traffic was stored to a pcap file. Analysing it on Wireshark displays all the packets transferred between the two devices and the attributes that were changed during the write process. Obviously there's not much data exchanged between an iPhone when it's working with a locking device so I was wondering, how it is possible to differentiate between encrypted and an unencrypted Bluetooth traffic in this case?
The first capture is from my mac which appears to use encryption
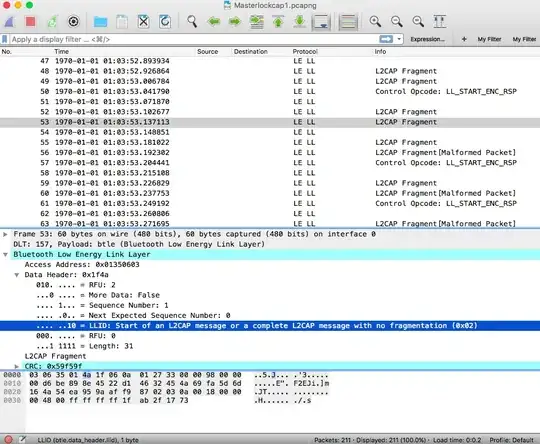
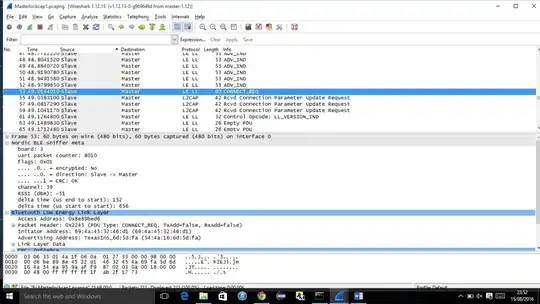
The other is the Wireshark in using on my Windows machine which has got all the plugins necessary to view the captured files from Nordic's nRF Sniffer software. I don't understand how the same file can be displayed with completely different information.