WPA was just a quick update to WEP protocol to solve some security problems until the final version of 802.11i standard was delivered.
The message integrity check, per-packet key hashing, broadcast key rotation, sequence counter and key mixing function were updated from WEP in order to patch some of the current vulnerabilities. This is why in some cases, WPA is considered to be a draft of 802.11i standard.
The main difference between WPA and WPA2 is the encryption protocol used:
TKIP used by WPA, still uses RC4 cipher as WEP, so apart from the patched vulnerabilities it has some new ones like MIC key recovery and an extended version of chop-chop WEP attack.
WPA2 was the final implementation of 802.11i and it introduces a new encryption protocol CCMP. This new protocol uses a stronger cipher AES-256, which represents a huge improvement from RC4.
Aside from this main difference, both WPA and WPA2 uses the same key exchange mechanism. The 4-way handshake is used to exchange encryption keys, so therefore this is why you can attack WPA/WPA2 in the same way, by capturing its handshake and bruteforcing PMK/PTK:
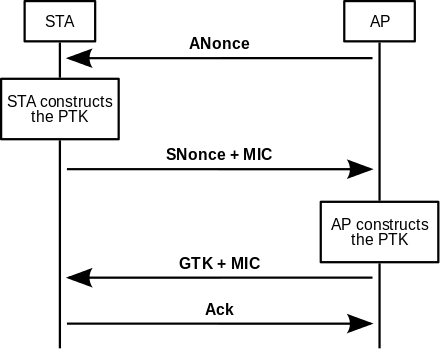
The attacker tries various passphrases, computes PMK and PTK using those passphrases, and then verifies the MAC in order to check if the passphrase was correct.
