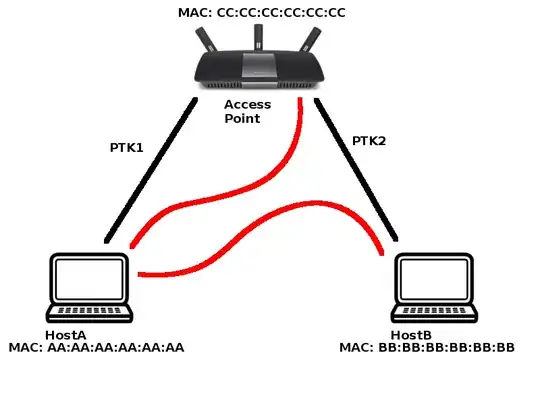
On wireless network running under WPA2 protocol, the communication between a client and the AP is encrypted using a session key (calling it that way, but if there's a more exact term I'd be glad to edit it) that is exchanged between them during the 4-way Handshake (which checks if said client is in possession of the PSK).
This session key is unique for each client connected to the AP. I'm assuming that statement since when an attacker is sniffing a network, he needs to have the handshake of each client if he wishes to decrypt every clients communication with the AP. So even if you're connected to said network, you won't be able to decrypt someone elses communication with the AP, since your session key is a different one (unless you happen to capture the 4-way handshake of the other client).
During a MiTM attack using ARP spoofing, you are already connected to the AP, but you don't have the other clients session keys. Once you poison their ARP cache, they will start sending the packets meant to be sent to the AP to your machine. The question is, since they still believe they are talking to the AP, won't they encrypt the packets using the session key that they exchanged with the AP during connection?
I ask that because experimenting (on my own network) I didn't need the 4-way handshake to see the decrypted traffic on the attacking machine, which I believed I'd need. I was wondering if maybe the session key is attached to the MAC address, so once the victim starts talking to your MAC, even though it believes you're the gateway, it will not encrypt the traffic with the session key it was using before.