I am newbie in information security I am trying to understand the difference between a digital signature and encryption of a message.
Lets consider simple example of email message.
I understand how each of methods works, but don't understand the real value of using one instead of another.
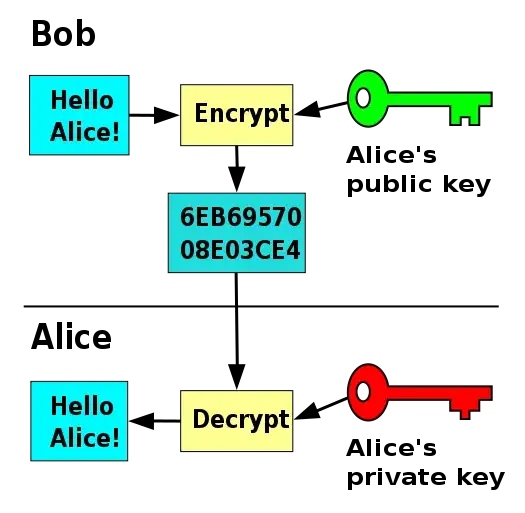
There are two parties anyway. For example Bob and Alice. Bob has generated a key pair (public + private).
Asymmetric encryption - message is encrypted by sender that has private key. Bob encrypts message with its private key, sends it to Alice, Alice as well as anyone else has access to Bob's public key, so Alice can decrypt and read message as well as encrypt an answer with Bob's public key and send it back.
a) Anyone can intercept communication and read Bob's message, but no one can encrypt new message and send it to Alice, because message can be only encrypted with private key.
b) Message integrity is obvious
Digital Signature Bobs calculates hash of plain text message, encrypts this hash with its private key and sends plain text message with a chunk of data called digital signature to Alice. Alice receives message, decrypts signature with Bob's public key, verifies if received message produces the same hash as was stored inside signature.
a) Anyone can modify message, but hash calculated by Alice won't be the same. Anyone can intercept and send its own message, but Alice is waiting for message from Bob and will try to decrypt signature with Bobs public key. b) Message integrity also obvious.
I don't understand a big difference between these two methods, I mean what is the value of each. In both methods we are using asymmetric encryption. Each method provides message integrity.
Please explain what is the main difference between these ways of encrypting data?