I have already tested how to do a MITM attack, using a fake AP to intercept the WPA-PSK, by presenting the user to a vendor (e.g. Linksys) logon page, before routing network traffic through eth0.
However, for someone with computer expertice this will probably not work.
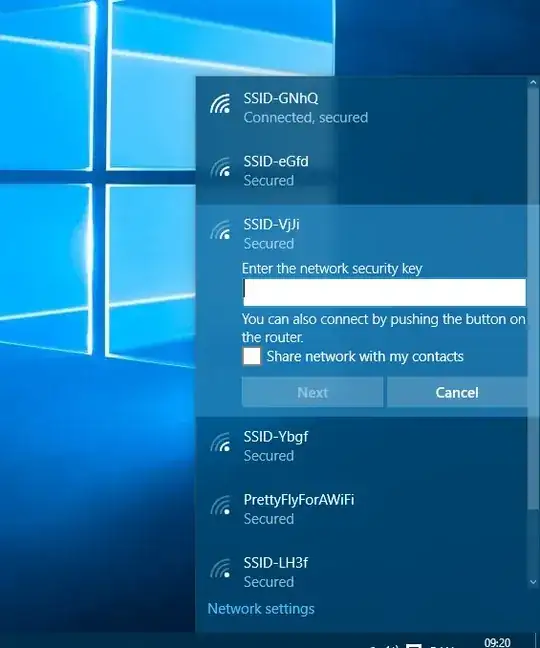
Instead of presenting the user with a fake logon page in the browser, is it then possible to intercept the passphrase from the Windows logon mechanism (seen below)? To be more specific, is it possible to configure the fake access point to fool Windows into requiring a passphrase (in the fashion below) and send it unencrypted to the AP? This would seem legitimate from the users point-of-view!
Normally, the AP created by airbase-ng is open and does not require logon credentials.