We intend to use McAfee ESM Nitro (SIEM) for security monitoring of our infrastructure servers. To bring automation in system administration of our servers, we have developed some applications in-house.
For instance, we are using a 3rd party tool for automated system automation which is Ansible and we have an in-house application that controls which of our server remains in production or whom to send out of production.
We now intend to integrate McAfee ESM Nitro with these two applications. So that whenever any threat alert is generated through Nitro, it should use Ansible or our in-house built application to run the remediation steps or locking out the system from our production environment.
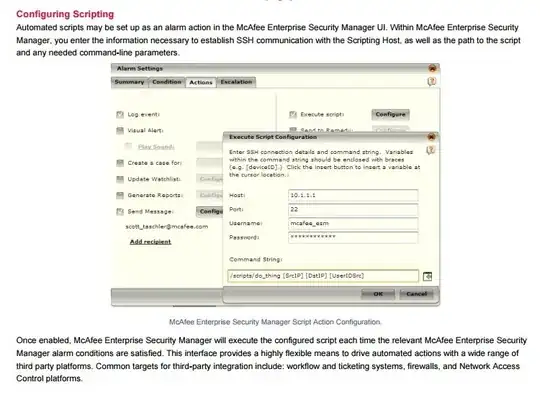
The Nitro provides two options for such actions to be triggered against any alert. Either to remotely connecting to a server using SSH and run any script residing over that server or running the script through any URL over HTTPS. Please find the snapshot attached for both the options.
I have read the thread over this website where the comparison between SSH and HTTPs is discussed (What is the difference between SSL vs SSH? Which is more secure?)
I would request for your professional advice as to which option to adapt for and which is more secure.
Thanks, Fahad.SIEM background URL option