As for your example; consider the shopping bill with injected malicious code, obviously a PDF can be injected with a malware - take a look at how they inject into it.
Spammers try to obtain as many valid email addresses as possible, i.e.
actually used by users. They use different techniques for this, some
of which are highly sophisticated:
Mail lists: the spammer looks in the mail list and notes down the addresses of the other members.
Purchasing user databases from individuals or companies: although this type of activity is illegal, it is actually carried out in
practice and there is a black market.
Use of robots (automatic programs) that scour the Internet looking for addresses in web pages, newsgroups, weblogs, etc.
DHA (Directory Harvest Attack) techniques: the spammer generates email addresses belonging to a specific domain and sends messages to
them. The domain mail server will respond with an error to those
addresses that do not actually exist, so the spammer can discover
which addresses generated are valid. The addresses can be compiled
using a dictionary or through brute force, i.e. by trying all possible
character combinations.
Consequently, all email users are at risk from these types of attacks.
Any address published on the Internet (used in forums, newsgroups or
on any website) is more likely to be a spam victim.
Techniques used.
Spammers use numerous techniques to produce messages capable of
by-passing all types of mail filters. Some of the tricks used to
obscure the message’s HTML code are looked at below:
Division of message subject line using bogus line breaks:
Subject: =?utf-8?q?Identical drugs -- l?=
=?utf-8?q?ittle monetary valu?=
=?utf-8?q?e!?=
Use of null characters (Quoted-Printable type encoding): =00H=00T=00M=00L=00>=00<=00H=00E=00A=00D=00>=00=0D=00=0A=00<=00M=00E=00=
T=00A=00 =00h=00t=00t=00p=00-=00e=00q=00u=00i=00v=00=3D=00C=00o=00n=00=
t=00e=00n=00t=00-=00T=00y=00p=00e=00 =00c=00o=00n=00t=00e=00n=00t=00=3D=
=00"=00t=00e=00x=00t=00/=00h=00t=00m=00l=00;=00 =00c=00h=00a=00r=00s=00=
=00t=00=3D=00u=00n=00i=00c=00o=00d=00e=00"=00>=00=0D=00=0A=00<=00M=00=
E=00T=00A=00 =00c=00o=00n=00t=00e=00n=00t=00=3D=00"=00M=00S=00H=00T=00=
M=00L=00 =006=00.=000=000=00.=002=008=000=000=00.=001=004=000=000=00"=00=
=00n=00a=00m=00e=00=3D=00G=00E=00N=00E=00R=00A=00T=00O=00R=00>=00<=00=
/=00H=00E=00A=00D=00>=00=0D=00=0A=00<=00B=00O=00D=00Y=00>
Interchanging letters in the words used. The message is still legible
to the recipient, but the filters do not recognize the words used:
I finlaly was able to lsoe the wieght I have been sturggling to
lose for years! And I couldn't bileeve how simple it was! Amizang
pacth makes you shed the ponuds! It's Guanarteed to work or your
menoy back!
Inverting text using the Unicode right-to-left override, expressed as HTML entities (? y ?):
Your Bnak Cdra Linknig
(Your Bank Card Linking)
Encapsulating a tag with an HREF tag, so that a legitimate URL appears instead of a malicious one.
<A HREF="<URL_LEGÍTIMA>">
<map name="FPMap0">
<area coords="0, 0, 623, 349" shape="rect" href="<URL_MALICIOSA>">
</map>
<img SRC="<img_url>" border="0" usemap="#FPMap0">
</A>
Use of ASCII characters to “design” the message content:
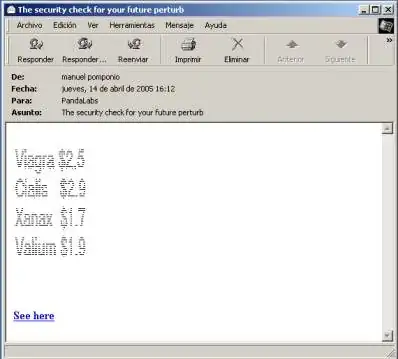
Although some of the techniques used have now been mentioned, there
are many more, such as the use of incorrect HTML tags, URL encoding,
the use of HTML entities to conceal certain letters, the use of
invisible ink, etc.
Other types of techniques are based on including the spam message as
an attached file in a valid message or the use of CSS (Cascading Style
Sheets) in spam messages to conceal certain words or parts of the
message.
Methods used for spam distribution are as follows:
Vulnerable or poorly configured mail servers (Open Relay) which allow any user to send messages without checking their sender (which
will normally be spoofed).
Computers affected by malware: certain types of malware facilitate the sending of spam through affected computers, such as the
installation of proxy. servers. It is even possible to rent botnets,
real computer networks affected by bots (hybrids of worms, Trojans y
backdoors).
The basic rule for attacker is to trick you and steal your stuff, don't give fall for it.
