Restriction (mathematics)
In mathematics, the restriction of a function is a new function, denoted or , obtained by choosing a smaller domain A for the original function .
| Function | |||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| x ↦ f (x) | |||||||||||||||||||||||||||||||||
| Examples by domain and codomain | |||||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||||
| Classes/properties | |||||||||||||||||||||||||||||||||
| Constant · Identity · Linear · Polynomial · Rational · Algebraic · Analytic · Smooth · Continuous · Measurable · Injective · Surjective · Bijective | |||||||||||||||||||||||||||||||||
| Constructions | |||||||||||||||||||||||||||||||||
| Restriction · Composition · λ · Inverse | |||||||||||||||||||||||||||||||||
| Generalizations | |||||||||||||||||||||||||||||||||
| Partial · Multivalued · Implicit | |||||||||||||||||||||||||||||||||
Formal definition
Let be a function from a set E to a set F. If a set A is a subset of E, then the restriction of to is the function[1]
given by f|A(x) = f(x) for x in A. Informally, the restriction of f to A is the same function as f, but is only defined on .
If the function f is thought of as a relation on the Cartesian product , then the restriction of f to A can be represented by its graph, where the pairs represent ordered pairs in the graph G.
Examples
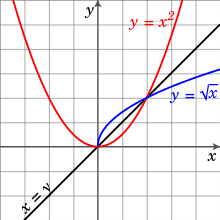
- The restriction of the non-injective function to the domain is the injection.
- The factorial function is the restriction of the gamma function to the positive integers, with the argument shifted by one:
Properties of restrictions
- Restricting a function to its entire domain gives back the original function, i.e., .
- Restricting a function twice is the same as restricting it once, i.e. if , then .
- The restriction of the identity function on a set X to a subset A of X is just the inclusion map from A into X.[2]
- The restriction of a continuous function is continuous.[3][4]
Applications
Inverse functions
For a function to have an inverse, it must be one-to-one. If a function f is not one-to-one, it may be possible to define a partial inverse of f by restricting the domain. For example, the function
defined on the whole of is not one-to-one since x2 = (−x)2 for any x in . However, the function becomes one-to-one if we restrict to the domain , in which case
(If we instead restrict to the domain , then the inverse is the negative of the square root of y.) Alternatively, there is no need to restrict the domain if we don't mind the inverse being a multivalued function.
Selection operators
In relational algebra, a selection (sometimes called a restriction to avoid confusion with SQL's use of SELECT) is a unary operation written as or where:
- and are attribute names,
- is a binary operation in the set ,
- is a value constant,
- is a relation.
The selection selects all those tuples in for which holds between the and the attribute.
The selection selects all those tuples in for which holds between the attribute and the value .
Thus, the selection operator restricts to a subset of the entire database.
The pasting lemma
The pasting lemma is a result in topology that relates the continuity of a function with the continuity of its restrictions to subsets.
Let be two closed subsets (or two open subsets) of a topological space such that , and let also be a topological space. If is continuous when restricted to both and , then is continuous.
This result allows one to take two continuous functions defined on closed (or open) subsets of a topological space and create a new one.
Sheaves
Sheaves provide a way of generalizing restrictions to objects besides functions.
In sheaf theory, one assigns an object in a category to each open set of a topological space, and requires that the objects satisfy certain conditions. The most important condition is that there are restriction morphisms between every pair of objects associated to nested open sets; i.e., if , then there is a morphism resV,U : F(U) → F(V) satisfying the following properties, which are designed to mimic the restriction of a function:
- For every open set U of X, the restriction morphism resU,U : F(U) → F(U) is the identity morphism on F(U).
- If we have three open sets W ⊆ V ⊆ U, then the composite resW,V o resV,U = resW,U.
- (Locality) If (Ui) is an open covering of an open set U, and if s,t ∈ F(U) are such that s|Ui = t|Ui for each set Ui of the covering, then s = t; and
- (Gluing) If (Ui) is an open covering of an open set U, and if for each i a section si ∈ F(Ui) is given such that for each pair Ui,Uj of the covering sets the restrictions of si and sj agree on the overlaps: si|Ui∩Uj = sj|Ui∩Uj, then there is a section s ∈ F(U) such that s|Ui = si for each i.
The collection of all such objects is called a sheaf. If only the first two properties are satisfied, it is a pre-sheaf.
Left- and right-restriction
More generally, the restriction (or domain restriction or left-restriction) A ◁ R of a binary relation R between E and F may be defined as a relation having domain A, codomain F and graph G(A ◁ R) = {(x, y) ∈ G(R) | x ∈ A} . Similarly, one can define a right-restriction or range restriction R ▷ B. Indeed, one could define a restriction to n-ary relations, as well as to subsets understood as relations, such as ones of E × F for binary relations. These cases do not fit into the scheme of sheaves.
Anti-restriction
The domain anti-restriction (or domain subtraction) of a function or binary relation R (with domain E and codomain F) by a set A may be defined as (E \ A) ◁ R; it removes all elements of A from the domain E. It is sometimes denoted A ⩤ R.[5] Similarly, the range anti-restriction (or range subtraction) of a function or binary relation R by a set B is defined as R ▷ (F \ B); it removes all elements of B from the codomain F. It is sometimes denoted R ⩥ B.
See also
References
- Stoll, Robert (1974). Sets, Logic and Axiomatic Theories (2nd ed.). San Francisco: W. H. Freeman and Company. pp. 5. ISBN 0-7167-0457-9.
- Halmos, Paul (1960). Naive Set Theory. Princeton, NJ: D. Van Nostrand. Reprinted by Springer-Verlag, New York, 1974. ISBN 0-387-90092-6 (Springer-Verlag edition). Reprinted by Martino Fine Books, 2011. ISBN 978-1-61427-131-4 (Paperback edition).
- Munkres, James R. (2000). Topology (2nd ed.). Upper Saddle River: Prentice Hall. ISBN 0-13-181629-2.
- Adams, Colin Conrad; Franzosa, Robert David (2008). Introduction to Topology: Pure and Applied. Pearson Prentice Hall. ISBN 978-0-13-184869-6.
- Dunne, S. and Stoddart, Bill Unifying Theories of Programming: First International Symposium, UTP 2006, Walworth Castle, County Durham, UK, February 5-7, 2006, Revised Selected ... Computer Science and General Issues). Springer (2006)