Echo (communications protocol)
Echo (one-to-all, one-to-one, or one-to-some distribution) is a group communications protocol where authenticated and encrypted information is addressed to members connected to a node.
| Routing schemes |
|---|
| Unicast |
| Broadcast |
| Multicast |
| Anycast |
| Geocast |
Adaptive Echo, Full Echo, and Half Echo can be chosen as several modes of the encrypted Echo protocol.
The Echo protocol offers three modes of operation: Adaptive Echo, Full Echo, and Half Echo.
Adaptive Echo

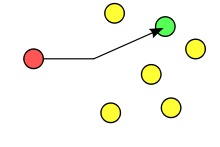
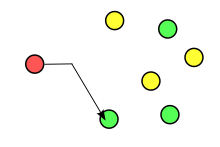
The Adaptive Echo distributes messages to parties that have shown awareness of a secret token. The graphic at the side shows the communication example of Hansel and Gretel. Referring to the old fairy tale, both highlight the trees with either "white pebbles" or "bread crumbs" to discover each other in the forest. They wish to communicate without the wicked witch knowing. How can Hansel and Gretel communicate without revealing their communications? The nodes in this example use token "white pebbles". Because the wicked witch is unaware of the secret token, she will not receive communications from Hansel and Gretel unless, of course, she misbehaves.[1]
Full Echo
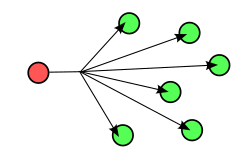
Full Echo or simply Echo sends each message to every neighbor. Every neighbor does the same unless it's the target node of a specific message. In smaller networks, the message should reach every peer. Nodes can be client, server, or both.
Half Echo
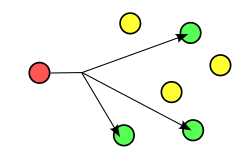
The Half Echo sends the message only to a direct neighbor. If configured correctly, the target node will not disperse the received message to other nearby nodes. This allows two neighbors to communicate with each other on dedicated sockets. That is, data from other nodes will not traverse the restricted socket. Though always authenticated and encrypted, the nodes can exclude others from knowing about the communications.[2]
Echo Accounts
Accounts allow for exclusive connections. A server node may establish accounts and then distribute the credentials information. Accounts create an artificial web of trust without exposing the public encryption key and without attaching the key to an IP address.
References
- "User Manual" (PDF). GoldBug. Retrieved 16 August 2014.
- Weller, Jan. "Testbericht zu GoldBug". Freeware.de. Retrieved 16 August 2014.