Clam AntiVirus
Clam AntiVirus (ClamAV) is a free software, cross-platform and open-source antivirus software toolkit able to detect many types of malicious software, including viruses. One of its main uses is on mail servers as a server-side email virus scanner. The application was developed for Unix and has third party versions available for AIX, BSD, HP-UX, Linux, macOS, OpenVMS, OSF (Tru64) and Solaris. As of version 0.97.5, ClamAV builds and runs on Microsoft Windows.[1][2] Both ClamAV and its updates are made available free of charge.
 | |
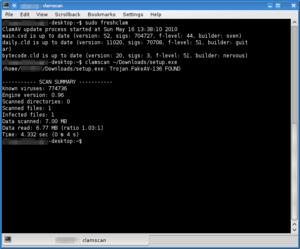 Clam AV 0.96, running a definition update, scanning a file and identifying a Trojan from the command-line. | |
| Developer(s) | Cisco Systems |
|---|---|
| Stable release | 0.102.4
/ July 16, 2020 |
| Repository | |
| Written in | C, C++ |
| Operating system | Cross-platform |
| Type | Antivirus software |
| License | GNU General Public License |
| Website | www |
Sourcefire, a maker of intrusion detection products and the owner of Snort, announced on 17 August 2007 that it had acquired the trademarks and copyrights to ClamAV from five key developers.[3] Upon joining Sourcefire, the ClamAV team joined the Sourcefire Vulnerability Research Team (VRT). In turn, Sourcefire was acquired by Cisco in 2013.[4] The Sourcefire VRT became Cisco Talos,[5] and ClamAV development remains there.
Features
ClamAV includes a number of utilities: a command-line scanner, automatic database updater and a scalable multi-threaded daemon, running on an anti-virus engine from a shared library.[1]
The application also features a Milter interface for sendmail and on-demand scanning. It has support for Zip, RAR, Tar, Gzip, Bzip2, OLE2, Cabinet, CHM, BinHex, SIS formats, most mail file formats, ELF executables and Portable Executable (PE) files compressed with UPX, FSG, Petite, NsPack, wwpack32, MEW, Upack and obfuscated with SUE, Y0da Cryptor. It also supports many document formats, including Microsoft Office, HTML, Rich Text Format (RTF) and Portable Document Format (PDF).[1]
The ClamAV virus database is updated at least every four hours and as of 10 February 2017 contained over 5,760,000 virus signatures with the daily update Virus DB number at 23040.[6][7]
Effectiveness
ClamAV is currently tested daily in comparative tests against other antivirus products on Shadowserver. In 2011, Shadowserver tested over 25 million samples against ClamAV and numerous other antivirus products. Out of the 25 million samples tested, ClamAV scored 76.60% ranking 12 out of 19, a higher rating than some much more established competitors.[8]
In the 2008 AV-Test, which compared ClamAV to other antivirus software, it rated: on-demand: very poor; false positives: poor; response time: very good; rootkits: very poor.[9]
In a Shadowserver six-month test between June and December 2011, ClamAV detected over 75.45% of all viruses tested, putting it in fifth place behind AhnLab, Avira, BitDefender and Avast. AhnLab, the top antivirus, detected 80.28%.[10]
Unofficial databases
The ClamAV engine can be reliably used to detect several kinds of files. In particular, some phishing emails can be detected using antivirus techniques. However, false positive rates are inherently higher than those of traditional malware detection.[11]
There are several unofficial databases for ClamAV:
- Sanesecurity is an organization that maintains a number of such databases; in addition they distribute and classify a number of similar databases from other parties, such as Porcupine, Julian Field, MalwarePatrol.[12]
- SecuriteInfo.com also provides additional signatures for ClamAV.[13]
ClamAV Unofficial Signatures are mainly used by system administrators to filter email messages.[14] Detections of these groups should be scored, rather than causing an outright block of the "infected" message.[12]
Platforms
Linux, BSD
ClamAV is available for Linux and BSD-based operating systems.[1] In most cases it is available through the distribution's repositories for installation.
On Linux servers ClamAV can be run in daemon mode, servicing requests to scan files sent from other processes. These can include mail exchange programs, files on Samba shares, or packets of data passing through a proxy server.
On Linux and BSD desktops ClamAV provides on-demand scanning of individual files, directories or the whole PC.[1]
macOS
Apple macOS Server has included ClamAV since version 10.4. It is used within the operating system's email service. A paid-for graphical user interface is available from Canimaan Software Ltd[15] in the form of ClamXav.[16] Additionally, Fink, Homebrew and MacPorts have ported ClamAV.
Another program which uses the ClamAV engine, on macOS, is Counteragent. Working alongside the Eudora Internet Mail Server program, Counteragent scans emails for viruses using ClamAV and also optionally provides spam filtering through SpamAssassin.
OpenVMS
ClamAV for OpenVMS is available for DEC Alpha and Itanium platforms. The build process is simple and provides basic functionality, including: library, clamscan utility, clamd daemon and freshclam for update.[17]
Windows
ClamAV for Windows is now a part of the Immunet client produced by Cisco. Immunet is a real-time cloud based detection software, maintained by Cisco, which owns both ClamAV and Immunet.[18]
eComStation
ClamAV for eComStation (OS/2) is available from OS/2 Power Wiki. "The main purpose of this software is the integration with mail servers (attachment scanning). The package provides a flexible and scalable multi-threaded daemon, a command line scanner, and a tool for automatic updating via Internet. The programs are based on a shared library distributed with the Clam AntiVirus package, which you can use with your own software. Most importantly, the virus database is kept up to date."[19]
Graphical interfaces
Since ClamAV does not include a graphical user interface (GUI) but instead is run from the command line, a number of third-party developers have written GUIs for the application for various platforms and uses.
These include:
- Linux
- macOS
- ClamXav is a port which includes a graphical user interfaces and has a "sentry" service which can watch for changes or new files in many cases. There is also an update and scanning scheduler through a cron job facilitated by the graphical interface. ClamXav can detect malware specific to macOS, Unix, or Windows. The ClamXav application and the ClamAV engine are updated regularly.[24] ClamXav is written and sold by Canimaan Software Ltd.[15]
- Tiger Cache Cleaner is shareware software which installs and presents a graphic interface for using ClamAV to scan for viruses, and provides other unrelated functions.
- Microsoft Windows
- Immunet
- ClamWin
- CS Antivirus[25]
- Graugon AntiVirus[25]
- Clam Sentinel
ClamWin
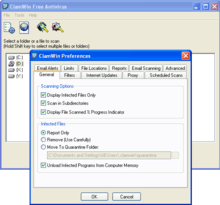
ClamWin is a graphical user interface front end for ClamAV for Microsoft Windows built by ClamWin Pty Ltd. Features include on-demand (user started) scanning, automatic updates, scan scheduling, context menu integration to Explorer, and an add-in for Microsoft Outlook. ClamWin does not provide on-access scanning, additional software must be used.
Plugins for Mozilla Firefox which use ClamWin to scan downloaded files are also available.[26][27] Several other extensions allow users to process downloaded files with any software and scan the files with ClamWin.[28][29][30][31]
Clam Sentinel
Clam Sentinel[32] is a free software system tray application that detects file system changes and scans the files modified using ClamWin in real-time.[33] It works with Windows 98/98SE/ME/XP/Vista/7/8. It features a real-time scanner for ClamWin, optional system change messages and proactive heuristic protection.
Real-time file scanning
Since Version 0.99, ClamAV supports on-access (real-time) scanning via the Linux kernel (version >= 3.8) module fanotify.[34] Alternatively, ClamAV can be used with other applications such as ClamFS (for any Unix-like operating system supporting FUSE) and Clam Sentinel (for Windows) to provide real-time checks.[35]
Patent lawsuit
In 2008, Barracuda Networks was sued by Trend Micro for its distribution of ClamAV as part of a security package.[36] Trend Micro claimed that Barracuda's utilization of ClamAV infringes on a software patent for filtering viruses on an Internet gateway. The free software community responded in part by calling for a boycott against Trend Micro. The boycott was also endorsed by the Free Software Foundation.[37] Barracuda Networks counter-sued with IBM-obtained patents in July 2008.[38] On May 19, 2011, the U.S. Patent and Trademark Office issued a Final Rejection[39] in the reexamination of Trend Micro's U.S. patent 5,623,600.[40]
See also
- List of antivirus software
- List of free and open-source software packages
- Software patents and free software
References
- ClamAV (2007). "About ClamAV". Retrieved 2008-12-25.
- ClamAV (2007). "ClamAV Packages and Ports". Archived from the original on 2008-07-20. Retrieved 2008-12-31.
- "Sourcefire acquires ClamAV". ClamAV. 2007-09-17. Archived from the original on 2007-12-15. Retrieved 2008-02-12.
- "Cisco Completes Acquisition of Sourcefire". cisco.com. 2013-10-07. Retrieved 2014-06-18.
- "Cisco Talos". 2018-01-19.
- "About ClamAV". Archived from the original on 2008-11-20. Retrieved 2008-12-25.
- "Latest Stable Release". Archived from the original on 2010-09-18. Retrieved 2010-08-21.
- "ShadowServer Yearly Stats". shadowserver.org. 2012-01-05. Archived from the original on 2011-06-25. Retrieved 2012-01-05.
- "Anti-virus comparison test of current anti-malware products, Q1/2008". AV-Test GmbH. 22 January 2008. Archived from the original on 15 July 2011. Retrieved 12 February 2008.
- "ShadowServer 180 Day Stats". shadowserver.org. 2011-08-16. Archived from the original on 2011-11-27. Retrieved 2011-12-16.
- Brad Wardman; Tommy Stallings; Gary Warner; Anthony Skjellum (5 August 2011). "High-Performance Content-Based Phishing Attack Detection" (PDF). uab.edu. Retrieved 19 March 2018.
- Sanesecurity Phishing, Scam and Malware signatures for ClamAV Archived 2015-09-10 at the Wayback Machine
- SecuriteInfo.com Add 4.000.000 signatures to ClamAV Antivirus
- "ClamAV Unofficial Signatures Updater". sourceforge.net. 24 May 2009. Retrieved 2 September 2014.
- "About us". ClamXAV. Retrieved 2017-07-15.
- ClamXav.com (n.d.). "ClamXAV.com". Retrieved 2009-01-24.
- Chupahin, Alexey (December 2008). "Clam AntiVirus OpenVMS Project News". Archived from the original on 2011-10-06. Retrieved 2008-12-25.
- "Immunet Online Protection". Archived from the original on 2015-05-24. Retrieved 2015-05-23.
- "OS/2 Power Wiki : ClamAV". January 2011. Archived from the original on 2010-10-03. Retrieved 2012-08-17.
- Mauroni, Dave (December 2008). "ClamTk Virus Scanner". Retrieved 2008-12-25.
- Mauroni, Dave (October 2008). "ClamTk README". Retrieved 2008-12-26.
- KlamAV F. (May 2006). "KlamAV - Main Page". Retrieved 2013-03-04.
- "wbmclamav project".
- ClamXav.com (November 2008). "ClamXav.com". Retrieved 2008-12-25.
- "CS Anti-Virus description". Softpedia.com. 2009-03-23. Retrieved 2010-11-09.
- "FireClam: Use ClamAV to scan Firefox downloads for viruses". Firefox Addons. Retrieved 2009-11-02.
- "ClamWin Antivirus Glue for Firefox". Firefox Addons. Archived from the original on 2012-12-20. Retrieved 2008-04-15.
- "Download Scan". Downloadstatusbar.mozdev.org. 2005-08-19. Retrieved 2010-11-09.
- Download Statusbar
- "Safe Download". Extensions.geckozone.org. Retrieved 2010-11-09.
- ClamWin Pty Ltd (2009). "About ClamWin Free Antivirus". Archived from the original on 2010-01-25. Retrieved 2009-03-13.
- Clam Sentinel (2014-09-01). "Clam Sentinel - Free Realtime Antivirus".
- Cyber Pillar. "Clam Sentinel - Making ClamWin Be Used In Real-Time". Retrieved 2014-09-01.
- https://blog.clamav.net/2016/03/configuring-on-access-scanning-in-clamav.html
- "Clam Sentinel". Retrieved 2014-06-19.
- "Trend Micro patent claim provokes FOSS community, leads to boycott". Linux.com. 2008-02-11. Retrieved 2008-02-12.
- "Boycott Trend Micro". Free Software Foundation. 2008-02-11. Retrieved 2008-02-12.
- Paul, Ryan (2008-07-02). "Barracuda bites back at Trend Micro in ClamAV patent lawsuit". Arstechnica.com. Retrieved 2012-02-14.
- "Ex Parte Reexamination" (PDF). U.S. Patent and Trademark Office. 2011-05-19. Retrieved 2015-10-04.
- "Anatomy of a Dying Patent - The Reexamination of Trend Micro's '600 Patent". Groklaw.net. 2011-06-13. Retrieved 2015-10-04.
Further reading
- An interview with ClamAV founder Tomasz Kojm archived version