Bandytown, West Virginia
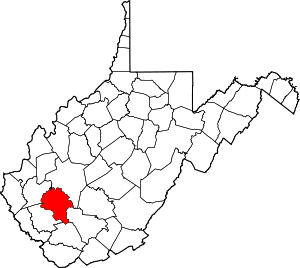
Bandytown is an unincorporated community in Boone County, West Virginia, United States. Bandytown is approximately 18 miles from Madison. Bandytown is accessible from Boone County Route 26, which is located right off West Virginia Route 85 at the Van Bridge split. The community has a total population of over 100 with approximately 70 homes.[2]
Bandytown | |
|---|---|
 View of Bandytown | |
 Bandytown Location within the state of West Virginia  Bandytown Bandytown (the United States) | |
| Coordinates: 37°56′26″N 81°38′23″W | |
| Country | United States |
| State | West Virginia |
| County | Boone |
| Time zone | UTC-5 (Eastern (EST)) |
| • Summer (DST) | UTC-4 (EDT) |
| ZIP codes | 25204 |
| GNIS feature ID | 1553796[1] |

Name
The community was named for George "Bandy" Green, an early settler on the West Fork. Bandytown was previously also known as "Chap" for Chapman Miller, a local merchant and postmaster.
Activities
Activities in Bandytown include all-terrain vehicle trails, a basketball court, fishing areas, and areas for skating/rollerblading. Van Elementary School and Van Junior/Senior High School, located 6 miles from Bandytown, are the closest public schools.
Bandytown has two churches: The Bandytown Church of Christ and The Martha Freewill Baptist Church, and three cemeteries: Greene Cemetery, Jarrell Cemetery, and Midferrell Cemetery.
The wet banana is a traditional Bandytown event that has been going on for years. The wet banana is a large water slide created by taking mining tarp and plastic and placing it on a large hill. Then, using water pumped from the creek mixed with some soap, people grab a tube and slide down.
In 2001, local residents Sue and Johnny Baire Jr. wrote and featured the hit song "God Bless Bandytown" on Sue's debut CD of the same title. The song mentions things near and dear to the hearts of Bandytown residents such as "the little white church" or "black berries." The song is considered an anthem for the town's website and it can be listened to on there in its entirety.
Bandytown is also the hometown of the "Dancing Outlaw" Jesco White.
Street names
| Street Names | County Route # |
|---|---|
| Bandy Green Branch Road | |
| Bulger Lane | |
| Carver Street | |
| Chap Road | 26 |
| Cherry Wood Circle | |
| Chester Lane | |
| Halona Lane | |
| Karla Lane | |
| Miller Addition Lane | 26^16 |
| Preston's Branch Road | 26^1 |
| Rosemont Drive | |
| Wilbarn Street | 26^15 |
Notable residents
- Jesco White, Mountain Dancer