0
I am using a MikroTik Router. I have two networks: 192.168.1.0/24 and 192.168.3.0/24. One is on ether4 and the other on ether5. I am trying to set it up such that these networks can ping each other.
Here is the router's config:
/interface ethernet
set [ find default-name=ether4 ] name=4_FrontDept
set [ find default-name=ether5 ] name=5_IntDept
set [ find default-name=ether9 ] name=9_BellNet
set [ find default-name=ether10 ] name=10_Primus
/ip pool
add name=InternetDept ranges=192.168.3.11-192.168.3.254
add name=FrontDept ranges=192.168.1.11-192.168.1.254
/ip dhcp-server
add address-pool=InternetDept disabled=no interface=5_IntDept name=\
InternetDept
add address-pool=FrontDept disabled=no interface=4_FrontDept name=FrontDept
/port
set 0 name=serial0
/interface pppoe-client
add ac-name="" add-default-route=no allow=pap,chap,mschap1,mschap2 \
dial-on-demand=no disabled=no interface=9_BellNet keepalive-timeout=60 \
max-mru=1480 max-mtu=1480 mrru=1600 name=Bellnet_ISP password={PASSWORD} \
profile=default service-name="" use-peer-dns=no user={USERNAME}
add ac-name="" add-default-route=no allow=pap,chap,mschap1,mschap2 \
dial-on-demand=no disabled=no interface=10_Primus keepalive-timeout=60 \
max-mru=1480 max-mtu=1480 mrru=1600 name=Primus_ISP password={PASSWORD} \
profile=default service-name="" use-peer-dns=no user={USERNAME}
/ip address
add address=192.168.3.1/24 interface=5_IntDept network=192.168.3.0
add address=192.168.1.1/24 interface=4_FrontDept network=192.168.1.0
/ip dhcp-server network
add address=192.168.1.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=192.168.1.1 \
netmask=24
add address=192.168.3.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=192.168.3.1 \
netmask=24
/ip dns
set allow-remote-requests=yes servers=8.8.8.8,8.8.4.4
/ip firewall mangle
add action=mark-connection chain=prerouting connection-mark=no-mark \
in-interface=Bellnet_ISP new-connection-mark=Bell
add action=mark-connection chain=prerouting connection-mark=no-mark \
in-interface=Primus_ISP new-connection-mark=Primus
add action=mark-connection chain=prerouting connection-mark=no-mark \
dst-address-type=!local in-interface=4_FrontDept new-connection-mark=Bell
add action=mark-connection chain=prerouting connection-mark=no-mark \
dst-address-type=!local in-interface=5_IntDept new-connection-mark=Primus
add action=mark-routing chain=prerouting connection-mark=Primus \
dst-address-type=!local new-routing-mark=RouteToPrimus
add action=mark-routing chain=prerouting connection-mark=Bell \
dst-address-type=!local new-routing-mark=RouteToBell
add action=mark-routing chain=prerouting comment=\
"For DNS Server On MikroTik Will Fetch Through Primus Connection" \
connection-mark=no-mark disabled=yes dst-port=53 new-routing-mark=\
RouteToPrimus protocol=udp
/ip firewall nat
add action=masquerade chain=srcnat connection-mark=Bell out-interface=\
Bellnet_ISP
add action=masquerade chain=srcnat connection-mark=Primus out-interface=\
Primus_ISP
/ip route
add distance=2 gateway=Primus_ISP routing-mark=RouteToPrimus
add distance=2 gateway=Bellnet_ISP routing-mark=RouteToBell
Tracert output from a 3.x computer to a 1.x one:
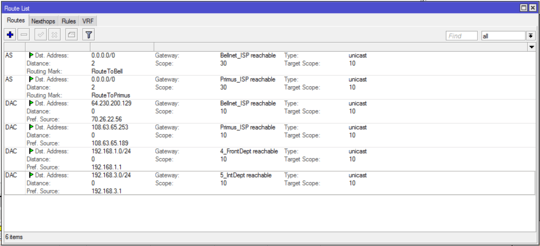
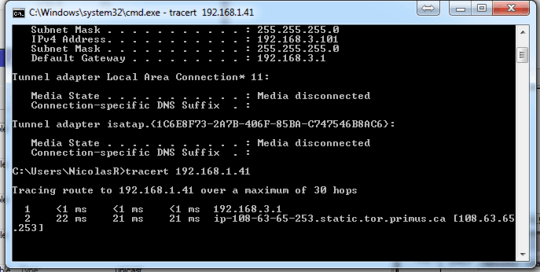
I'm not familiar with this specific firewall syntax, so perhaps I've missed where it explicitly allows local routing. I see rules that I think apply to !local (not local?) addresses; perhaps some rules that allow local traffic through are needed?
In the screenshot with tracert, if, for some reason, the interface 192.168.1.1 is down, that network would be !local, and traffic would then go out the primus conneciton. – Nevin Williams – 2015-09-29T19:08:29.310