4
2
Sometimes (maybe about once a day) I appear to have a quite high amount of incoming network traffic of around 2.5Mb/s during 15 minutes for no apparent reason. No P2P, nothing launched except browser and email and I even tried to stop them without changes.
My computer is a personal Mac OS X 10.10.4 (Yosemite) updated from Mac OS X 10.9.6 (Mavericks) and I’m the only owner. I have a script that rsync’s data on my local network every hour but it’s obviously not that. I also have a Synology app installed but it's closed and doesn't appear in ps aux or top.
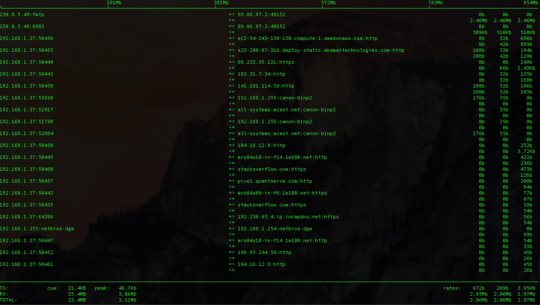
I investigated with iftop, so I can see where it’s comming from:
When I turn port display to numeric, FMTP is 8500, it corresponds to flight message protocol.
Then I tried to ping the IPs:
Buzut:~ Buzut$ ping 89.86.97.2
PING 89.86.97.2 (89.86.97.2): 56 data bytes
36 bytes from vl212.c6k04-t2.net.bbox.fr (62.34.0.182): Communication prohibited by filter
Vr HL TOS Len ID Flg off TTL Pro cks Src Dst
4 5 00 5400 abc7 0 0000 38 01 5abc 192.168.1.37 89.86.97.2
Request timeout for icmp_seq 0
36 bytes from vl212.c6k04-t2.net.bbox.fr (62.34.0.182): Communication prohibited by filter
Vr HL TOS Len ID Flg off TTL Pro cks Src Dst
4 5 00 5400 ae78 0 0000 38 01 580b 192.168.1.37 89.86.97.2
--- 89.86.97.2 ping statistics ---
2 packets transmitted, 0 packets received, 100.0% packet loss
Buzut:~ Buzut$ ping 239.0.5.49
PING 239.0.5.49 (239.0.5.49): 56 data bytes
Request timeout for icmp_seq 0
Request timeout for icmp_seq 1
Request timeout for icmp_seq 2
--- 239.0.5.49 ping statistics ---
4 packets transmitted, 0 packets received, 100.0% packet loss
What’s weird is that I’m 192.160.1.37 on my network but here it’s downloading data from 89.86.97.2 to 239.0.5.49 like if it just went through my computer without it to be the destination.
bbox.fr has something to do with my ISP because it’s Bouygues Telecom. But appart from that, it still look suspect to me. How can I know more? What is being downloaded? For what purpose?
At the same time, I don’t see this with netstat. The version of netstat in Mac OS X doesn’t work the same way as on other systems as far as options go. So here it goes:
Buzut$ netstat -a
Active Internet connections (including servers)
Proto Recv-Q Send-Q Local Address Foreign Address (state)
tcp4 0 0 192.168.1.37.50924 stackoverflow.co.https ESTABLISHED
tcp4 0 0 192.168.1.37.50922 190.93.245.58.http ESTABLISHED
tcp4 0 0 192.168.1.37.50918 ec2-23-21-110-17.http ESTABLISHED
tcp4 0 0 192.168.1.37.50917 ec2-23-21-110-17.http ESTABLISHED
tcp4 0 0 192.168.1.37.50912 104.16.12.8.http ESTABLISHED
tcp4 0 0 192.168.1.37.50799 a23-200-86-198.d.http ESTABLISHED
tcp4 0 0 192.168.1.37.50797 mrs04s09-in-f206.http ESTABLISHED
tcp4 0 0 192.168.1.37.50585 ip-228.net-89-3-.6690 ESTABLISHED
tcp4 0 0 localhost.cap *.* LISTEN
tcp4 0 0 localhost.1024 *.* LISTEN
tcp4 0 0 localhost.blackjack *.* LISTEN
tcp4 0 0 192.168.1.37.49468 stackoverflow.co.https ESTABLISHED
tcp46 0 0 *.53673 *.* LISTEN
tcp4 0 0 *.53673 *.* LISTEN
tcp4 0 0 192.168.1.37.49445 17.110.227.99.5223 ESTABLISHED
tcp4 0 0 localhost.27017 localhost.64807 ESTABLISHED
tcp4 0 0 localhost.64807 localhost.27017 ESTABLISHED
tcp4 0 0 *.27017 *.* LISTEN
tcp4 0 0 192.168.1.37.64286 192.230.65.4.ip..https ESTABLISHED
tcp4 143 0 192.168.1.37.58235 ns0.ovh.net.imap CLOSE_WAIT
tcp4 143 0 192.168.1.37.58232 ns0.ovh.net.imap CLOSE_WAIT
tcp4 143 0 192.168.1.37.58230 ns0.ovh.net.imap CLOSE_WAIT
tcp4 0 0 192.168.1.37.56996 17.172.239.102.5223 ESTABLISHED
tcp4 0 0 localhost.intu-ec-clie *.* LISTEN
tcp6 0 0 localhost.intu-ec- *.* LISTEN
tcp4 143 0 192.168.1.37.62687 ns0.ovh.net.imap CLOSE_WAIT
tcp4 0 0 localhost.ipp *.* LISTEN
tcp6 0 0 localhost.ipp *.* LISTEN
udp4 0 0 *.53878 *.*
udp4 0 0 *.62654 *.*
udp4 0 0 *.* *.*
udp46 0 0 *.53673 *.*
udp4 0 0 *.53673 *.*
udp4 0 0 *.54480 *.*
udp4 0 0 192.168.1.37.ntp *.*
udp6 0 0 buzut.ntp *.*
udp6 0 0 *.62268 *.*
udp4 0 0 *.62268 *.*
udp6 0 0 *.53100 *.*
udp4 0 0 *.53100 *.*
udp6 0 0 *.63111 *.*
udp4 0 0 *.63111 *.*
udp6 0 0 *.53310 *.*
udp4 0 0 *.53310 *.*
udp6 0 0 *.65513 *.*
udp4 0 0 *.65513 *.*
udp6 0 0 *.62913 *.*
udp4 0 0 *.62913 *.*
udp46 0 0 *.* *.*
udp4 0 0 *.* *.*
udp4 0 0 *.* *.*
udp4 0 0 *.* *.*
udp4 0 0 *.* *.*
udp4 0 0 *.54514 *.*
udp4 0 0 *.* *.*
udp4 0 0 *.* *.*
udp4 0 0 *.* *.*
udp6 0 0 localhost.ntp *.*
udp4 0 0 localhost.ntp *.*
udp6 0 0 localhost.ntp *.*
udp6 0 0 *.ntp *.*
udp4 0 0 *.ntp *.*
udp4 0 0 *.* *.*
udp4 0 0 *.* *.*
udp4 0 0 *.* *.*
udp4 0 0 *.* *.*
udp4 0 0 *.* *.*
udp4 0 0 *.* *.*
udp4 0 0 *.* *.*
udp46 0 0 *.* *.*
udp4 0 0 *.* *.*
udp4 0 0 *.* *.*
udp4 0 0 *.* *.*
udp6 0 0 *.mdns *.*
udp4 0 0 *.mdns *.*
udp4 0 0 *.* *.*
udp4 0 0 *.netbios-ns *.*
udp4 0 0 *.netbios-dgm *.*
To display port numbers I'd have to use
-Poption in iftop, then to see which process is running on a port I could donetstat -tunp | grep portNumberor evenlsof -i:portNumber– Buzut – 2015-08-15T08:35:40.513You say your ISP is Bouygues Telecom, but how is your internet connection handled? Meaning do you have DSL with a modem or are you using a Mi-Fi 3G/4G card or something similar? – JakeGould – 2015-08-31T00:05:40.570