0
I'm kind of new to setting up networking with ESXi and working with pfsense, so please excuse if this cannot be done or I'm asking something the wrong way.
I'm using ESXi 5.5.0 and I want to host some honeypots on my network that are accessible to the internet, but the honeypots themselves can't access anything outside of their subnet. Ideally I'd port forward specific ports like 21, 22, 80, 443 into various honeypot machines.
Now, I'm also hosting this at home, so I would like to segregate my honeypot network from my home network. My home network shouldn't be able to touch anything in the honeypot network, and vice-versa.
My current set up is this: Internet -> modem -> consumer router/switch combo. On that switch combo are my wireless devices and other home devices. Also attached to it is my ESXi server. My ESXi server also has the following network setup:
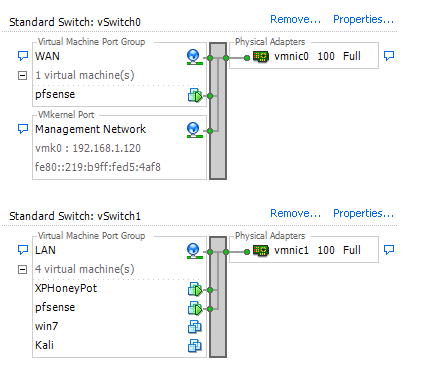
And my pfsense box has the following interfaces:
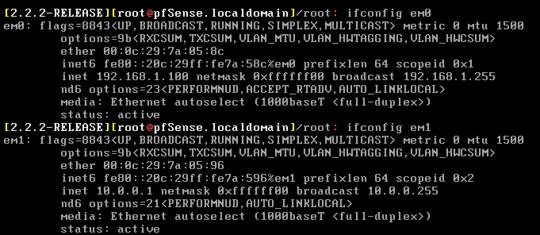
At this point, mostly everything is working except for two issues:
- Boxes in my honeypot network (10.0.0.x) can talk to boxes in my home network (192.168.1.x)
- DHCP server running on my pfsense LAN interface (em1) is handing out IP addresses that my comsumer router should be handing out. So when my phone connects to my wifi, it gets an address from pfsense, when it shouldn't be.
So my question is, how can I get this properly segregated so the two networks can't talk to each other and that DHCP isn't handing out addresses outside of its network?
Thanks! I really appreciate the help!
>
Should I add the iptables rule directly on pfsense from the command line, or is there a better way to do it through the web interface?
Yeah I was thinking about that, probably a good idea to set everything static.
Also yeah, definitely. Working on trying to get it accessible from the WAN, then shutting it off from LAN.
Most definitely. I'm going to give another hacker friend of mine remote access to get another set of eyes on it to see if he can find a way to break out.
Thanks for this reply! – Chiggins – 2015-05-20T17:28:22.533
@Chiggins it doesn't matter where you set the rule (web or cmd line) just make sure they get saved and that should do it. – DKNUCKLES – 2015-05-20T17:31:41.263