I don't think there is an easy way to do this on a mass scale. And you don't really mention the scope of these ssh connections. Terminal only? Might make things a bit easier.
Run ssh -NR 2210:localhost:22 intermediaryuser@intermediary.remote.machine.tld as someuser on the machine behind the firewall. I'm assuming 2210 is available on the intermediary machine; if it's not, pick another port. Each machine you want to access behind the firewall will need its own port.
Your Internet user connecting to the intermediary needs ssh access on the intermediary. To get behind the firewall just do ssh -t intermediaryuser@intermediary.remote.machine.tld "ssh someuser@localhost -p 2210" to get terminal access. You'll need to do the same thing on a different port for every server.
You can daemonize that first part so it happens on boot. I don't know the best way to, say, make it easy to manage two sets of logins, passwords, etc.. You can create passwordless logins based on ssh keys, but that will take time to set up and will need to be done for every user.
If terminal only works for you...
I created a little perl script to act as a login shell wrapper for a user called sshcatcher. I saved it to /usr/local/remote.pl:
#!/bin/perl
print "Please enter your username to access the firewalled server: ";
$user = <>;
chomp($user);
system("ssh", "$user\@localhost -p 2210");
With something like that, maybe you can chance allowing an account with an empty password on the intermediary to automate the process a little.
The vipw entry looks like:
sshcatcher:x:2000:2000::/home/sshcatcher:/usr/local/remote.pl
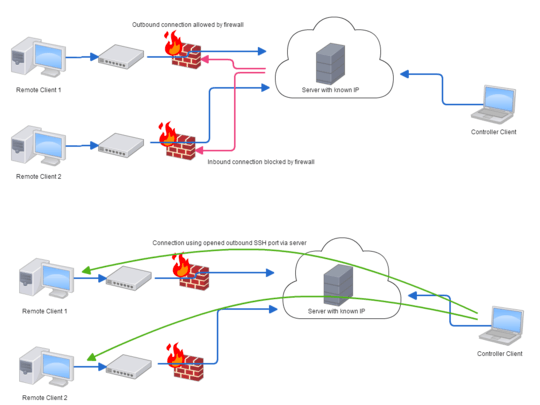
I am having trouble following this. The clients are behind a firewall, but they can ssh out to the new server you are setting up? – Paul – 2015-04-01T23:02:18.550
1the firewall (or router) is preventing inbound connection, meaning all connection needs to be outbound – Daniel – 2015-04-02T00:03:56.620
If they can all make outbound connections, what is stopping them connecting directly to the target server? Could you have a go at editing your question to make it clearer? There are multiple clients on different networks perhaps? – Paul – 2015-04-02T00:07:35.230
Sorry, but the term reverse SSH make no sense. SSH uses client\server architecture, it sounds like you are wanting to reverse those roles. If you did that it wouldn't be called reverse SSH; you'd simply be swapping the client and the server roles of each computer (IOW, you'd be installing the server software on a client [servers generally always have the client installed already]). This is one of those questions that I'd rather answer the question you should've asked instead of the question you did ask. – krowe – 2015-04-02T00:18:04.763
I've added a diagram that hopefully clears it up a little – Daniel – 2015-04-02T15:01:10.713
It sounds (and you even used the term yourself) that you want to use ssh -R which is a reverse connection. Perhaps you do not realize that you may use any number of -R connections? A single SSH server may forward to many different destinations. The incoming port determines the destination. – Daniel – 2015-04-02T15:06:19.037
I guess the issue I have is that I don't know how to manage these connections. How does the Controller Client know what remote clients it can connect to? How would the server deal with 20, 50 or 500 machines like this? – Daniel – 2015-04-02T15:28:17.207