1
I have a network, which has 2 nodes (a phone, a MacBook) both are connected to same wireless network, I know the SSID and password for the wireless network
password: mypassword
ssid: myssid
security: WPA2 Personal
I am currently running Wireshark on MacBook with following settings:
Edit > Preference > Capture > Interfaces > Edit
default buffer size `2048MiB`
default link layer header type: 802.11
monitor mode: checked

and to decrypt traffic under
Edit > Preference > Protocols > IEEE 802.11
Reassemble fragmented 802.11 datagram packets: checked
ignore vendor specific HT elements: unchecked
call subredisetor for retransmitted 802.11 frames: checked
assume packets have FCS: unchecked
Ignore the protection bit: Yes with IV
Enable decryption: checked
decryption keys:
key type: wpa-pwd
key: mypassword:myssid

I start it in capture mode: I make a http call to foobar.com from my phone, and I expected wireshark to pick it up and display in sniffed data, I don't see it there.
However, if I make same HTTP call to foobar.com from my mac, I can see it being listed.
Edit:
After that I see EAPOL handshake captured
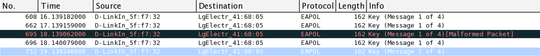
but still it is not able to decrypt packets captured for that source (Lg_Electr_41), also attached protocol preference

edit:
adding frame and data view of a random frame where source was Lg_Electr_41 from the same session where EAPOL was captured for this source
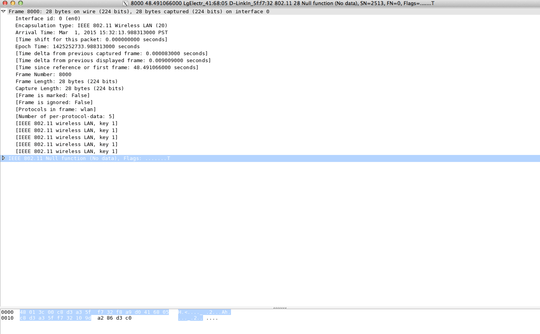
edit:
attaching requested frame
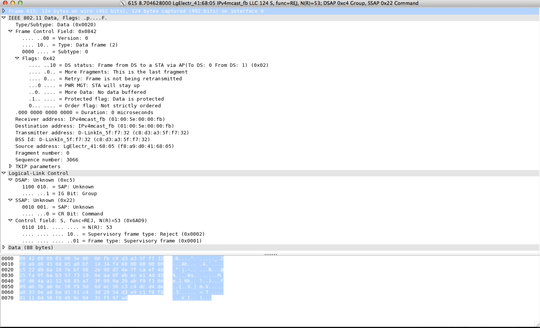
Thanks again for your help, I updated question with screenshot and more detail – user3833308 – 2015-03-01T22:32:23.470
It's decrypting them, but failing to dissect the resulting packets correctly, either because the decryption got the wrong results or the packets are somehow not laid out the way Wireshark expects. Could you show the packet details and both the "Frame" and decrypted data hex panes? – None – 2015-03-01T23:15:48.597
No, that's an 802.11 null frame, which has no data to decrypt. Try a frame such as frame 926, and open up the 802.11 and LLC layers. – None – 2015-03-02T02:29:10.213