Your requirement appears more or less similar to any corporation's VPN; you want your laptop to appear to be on your home network for the purposes of Internet access (and quite possibly other access).
I haven't used IPsec VPN's, and they should work fine when correctly configured, but I have done exactly what you're suggesting with OpenVPN servers on pfSense and OpenVPN clients on Windows, Linux, and Android for years, so I'll give you some guidance on the OpenVPN side of things.
First, the recommended reading:
- https://doc.pfsense.org/index.php/VPN_Capability_OpenVPN
- You want the Remote Access Server section
- https://www.highlnk.com/2013/12/configuring-openvpn-on-pfsense/
- You can skip the wizard and go right to the normal settings tabs that he goes to after the wizard.
- https://openvpn.net/index.php/open-source/documentation/howto.html
- Remember, all the GUI in pfSense does is write large parts of the config files for you, and generate a key or three.
Now, some recommendations for a high security setup, because that's what I believe in
- in PFsense, System, Cert Manager
- Create a CA for your VPN
- use SHA256 or SHA512 for the signature, and 2048 or 4096 bit RSA keys.
- Even on an ALIX (500Mhz single core, 256MB of RAM) I've found 4096 bit keys are fine.
- ideally, name it something like "VPN1Home_CA_2014Dec"
- You'll want this later when the next Heartbleed exploit pushes you to regenerate certs, and/or you want another VPN for another purpose, like a baby monitor
- Create a "Server" certificate for your VPN
- use SHA256 or SHA512 for the signature, and 2048 or 4096 bit RSA keys.
- Set the CA to the one you just created
- ideally, name it something like "VPN1Home_Server_2014Dec"
- Create a "Client" certificate for your laptop, and your phone, and whatever else you want
- Create a CRL, Certificate Revocation List for the CA
- you can leave it empty, but you might as well have one set in the VPN in case you do need to revoke a cert later.
- in pfSense, Services->OpenVPN
- WAN interface
- I like picking a port in the ephemeral range (49152 to 65535) rather than using the default https://en.wikipedia.org/wiki/Ephemeral_port
- checkmark TLS Authentication
- TLS Auth is why I wasn't nearly as concerned by Heartbleed as I could have been.
- let it create the key for you
- DH parameters length 2048 or 4096
- Even on an ALIX (500Mhz single core, 256MB of RAM) I've found 4096 bit keys are fine.
- Encryption algorithm
- ok, on an ALIX (500Mhz single core, 256MB of RAM) I stick with AES-128
- Pick Camellia or AES here, depending on what your client will support, at whatever length you like.
- Set your networks, obviously
- Redirect Gateway must be checked; this is the option that controls the "redirect-gateway def1" option
- i.e. sending all traffic through the VPN.
- which sends all your laptop traffic to your pfSense box, and then to the internet
- Don't use compression unless most of your internet data transfer is compressible
- Don't allow clients to talk to each other unless they need to
- Advanced: type in
- tls-cipher DHE-RSA-AES256-SHA
- NOTE: If you're using pure certificate based security, you DO NOT need to create pfSense users
- in pfSense, make sure DNS Forwarding/Resolver is set up.
- in pfSense, set up and/or validate your firewall rules
- WAN interface
- on the port you selected above, inbound, either TCP or UDP to match your VPN.
- turn on logging until you have things working, and perhaps after as well.
- OpenVPN interface
- on the IP range you assigned to VPN clients, PASS UDP on DNS (53) to the x.y.z.1 address of the tunnel network, so clients can get DNS through the VPN.
- on the IP range you assigned to VPN clients, PASS UDP on NTP (123) to the x.y.z.1 address of the tunnel network, so clients can get time sync through the VPN.
- turn on logging on these at least until you have things working
- For your clients
- You CAN use the pfSense Package that exports OpenVPN client configurations if you like
- You can also simply download the binary packages
- Android: OpenVPN for Android by Arne Schwabe
- Windows: OpenVPN Community client
- Linux: Use your distro's OpenVPN package
- You will need the following files:
- System, Cert Manager, CA, the Certificate of your CA only
- DO NOT DOWNLOAD THE KEY!!! ONLY THE CERTIFICATE
- name it whatever you like, perhaps the descriptive name you already made!
- used in the "ca ca.crt" client config line
- obviously replace ca.crt with your descriptive filename.
- System, Cert Manager, Certificates, the client certificate and key
- yes, for this one, the key also
- name it whatever you like, perhaps the descriptive name you already made!
- client cert used in the "cert client.crt" client config line
- obviously replace client.crt with your descriptive filename.
- client key used in the "cert client.key" client config line
- obviously replace client.key with your descriptive filename.
- Services, OpenVPN, your VPN, the TLS Shared Key
- just copy and paste from the text box into a text file, whose default name is "ta.key"
- used in the "tls-auth ta.key 1" client config line
- obviously replace ta.key with your filename.
- Edit your config as required, through the GUI or editing the .conf file yourself as you see fit
- Match the parameters you set in the server; the references will help, or you can look up pfSense's OpenVPN server config file and simply read it; except for the 1 vs 0 on tls-auth, most of the cipher parms are the same for both.
- don't forget to add the tls-cipher
- tls-cipher DHE-RSA-AES256-SHA
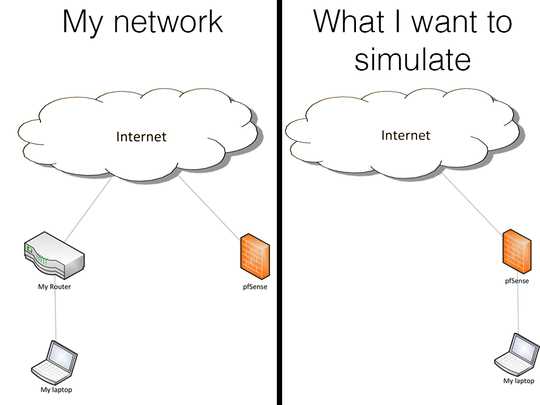
The picture was very helpful; for anyone who can no longer see it, the desired "virtual" config looked like
Internet
|
pfSense
|
Laptop
Note that the actual config I'm suggesting is:
Internet (coming from pfSense's location)
|
pfSense
|
Internet (only an OpenVPN connection)
|
Laptop
Additional link that may or may not be useful to you: http://pfsensesetup.com/video-pfsense-vpn-part-three-openvpn-pt-1/