There are commercial products like Check Point former "VSX" Systems which serve "virtual firewalls" on a given hardware base. If we talk about VMWare or better cloud based firewalling. You setup a firewall "in" the cloud to segment the "internal" cloud "network" not the communication between a cloud and another network.
The performance is very limited and the performance in a cloud is shared. An asic-based firewall can do > 500GBps. A VMware based Firewall or switch does < 20GBps. To the statement LAN NIC could catch a flu from wire. You also could state that any intermediate device like switch, router, ips could also get exploited by in-transit-traffic.
We see this in "malformed" packets (aka frames, fragments, segments etc.) So one could state using "intermediate" devices is insecure. Also the German NIST called BSI stated some years ago that the virtual routers (like VDCs (Virtual Device Context - Cisco Nexus)) and VRF (Virtual Route Forwarding) is insecure. From a point of view, sharing resources is always a risk. User can exploit resources and reduce service quality for all other users. Which globally would place the whole VLAN and overlay technologies (like VPN and MPLS) in Question.
If you have really high demands on security I would use dedicated hardware and dedicated network (including dedicated lines!) If you ask if the hypervisor (especially in bare metal) is a special security problem in a common scenario... I would say no.
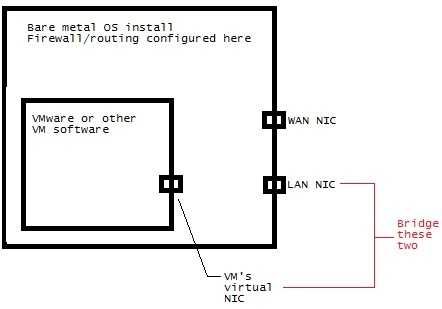
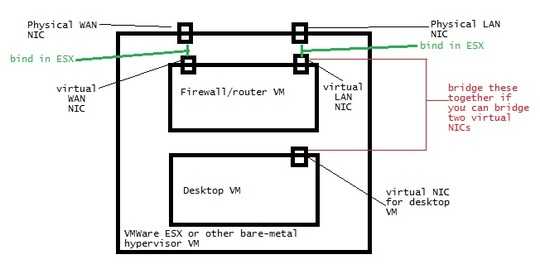
If your desktop is running on the bare metal, and your firewall is not, traffic going through your firewall still has to pass through the desktop OS before being examined by the firewall. So the firewall gives less protection here. – LawrenceC – 2015-03-21T17:34:10.500
upvoting you for the not-so-crappy paint illustration... thank you for your effort....
This approach would stop me from using most of the virtualization distros right? Particularly the likes of proxmox or vmware esx... – Nithin – 2014-03-11T15:41:17.410
IIRC Proxmox is based on Linux - and you can just configure your routing and firewall outside of any VM on that. There's no way to get outside of any VM on ESX AFAIK except a diagnostic mode so you probably don't want to use that. However, running two VM's "side by side" in ESX, where one is a "front end" for another (your "desktop VM" would only have a virtual NIC that's connected to the "firewall" VM), would be OK. The "desktop VM" couldn't directly do anything to the hypervisor in that case. – LawrenceC – 2014-03-11T16:41:53.363
I am planning to go with proxmox... I was planning to use something like ipfire or clearos... but if I have to install it on proxmox... I dont think I'll be able to use any of those either :( Also, is there a way to do something like diagram 2 with proxmox? Wouldnt diagram 2 scheme have the issues u mentioned in paragraph 3? – Nithin – 2014-03-11T17:15:12.063
Basically, if your router/firewall is in a VM, and your desktop is in a VM "behind" it, it's fine. If you are trying to setup a router/firewall VM "within" a desktop NOT in a VM is where security could be an issue. Diagram 2 is possible with Proxmox if you set up 2 VMs - one for your firewall/router VM and another for your desktop VM. – LawrenceC – 2014-03-11T17:49:03.843
That comment confuses me... correct me if I am wrong... If the firewall/router is in a virtualization server like proxmox or vmware ESX, there are no security issues. But if the firewall/router is in something like virtualbox in a full fledged desktop, the security issues u mentioned applies. What I am trying to setup is diagram 2 with other VMs and physical machines in the network connecting to the firewall's virtual LAN NIC for access to wan... does this scenario have the security issues? – Nithin – 2014-03-11T18:25:20.663