3
1
I am implementing a solution that requires client certificates. I'm using IIS 7.5 and ASP.Net 4 WCF services.
I've set the SSL Settings to Require SSL and require client certificates. Looks good so far. Because I'm new to the use of client certificates I've been doing a bit of research, and came across a Microsoft support article that attempts to explain a bit about the client certificate validation process. It states:
When the server prompts for a certificate, the request includes a list of the certification authorities that the server trusts. The client then compares this list to the list of certification authorities that the client trusts and creates a list of the ones that match. Then, the client compares that list to the client certificates it has and determines which, if any, certificates have been issued by certification authorities that both the client and the server trust.
Apparently the client will send certificates that both sides trust. What I'm interested in is can I configure IIS or my WCF service to only accept certain client certificates, such as ones we generate from our own certificate authority specifically for the purpose of this WCF service.
What is to stop someone using a client certificate from VeriSign or use from our certificate authority that were intended for some other purpose?
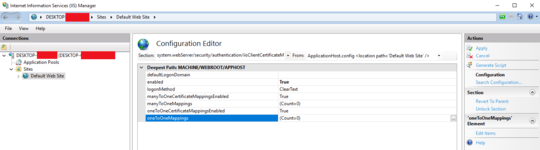
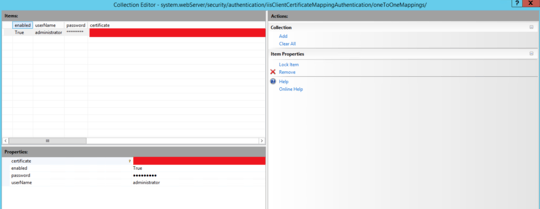
@Jeremy did you ever find a solution to this problem? – ahsteele – 2017-01-24T20:31:52.503
@ahsteele I haven't. In our environment we are using a reverse proxy mechanism (F5 is the vendor) so we enforce the client certificate there. We are able to write a script that ensures the client certificate is one that we've issued. It doesn't allow us to validate that the certificate is the one for that specific user though. If you figure out how to do this in IIS I'd like to know too... :) – Jeremy – 2017-01-24T21:26:43.597
@Jeremy was hoping you had the silver bullet. I'm guessing in your scenario the user is also being presented with a list of certificates from all of the CAs that both the server and client trust. – ahsteele – 2017-01-24T22:13:19.320
@ahsteele - in our case it's actually software that makes the request, not a user browsing, so the software is configured for a specific certificate. So the user doesn't have to pick a certificate and be presented with that choice. – Jeremy – 2017-01-25T17:23:46.493
@ahsteele - in a wcf service you can write a custom certificate validator. See https://msdn.microsoft.com/en-us/library/ms733806(v=vs.110).aspx and https://msdn.microsoft.com/en-us/library/aa354512(v=vs.110).aspx
– Jeremy – 2017-01-25T17:26:25.273The client does not send a certificate. It accepts one of the certificates offered by the server after validating against local certificates. – Brian – 2014-01-14T19:02:29.630
2@Brian - I don't understand. we're talking about client certificates. The server side requires the client to prove their identity by supplying a client certificate to the server, does it not? How does the client not send a certificate? – Jeremy – 2014-01-15T20:55:23.673