1
I have a web server sitting behind a NAT. The web server therefore has two IP addresses: one that is world visible, and one that is visible only on the LAN.
For the purpose of mobile devices, I would like to be able to refer to pages on the server from a single address, e.g. www.myhost.com in both cases, instead of using the local IP address such as 192.168.1.x when the device is on the LAN and www.myhost.com when the device is outside the LAN. There are two reasons for this: first, it is rather inconvenient to have to manually switch between addresses based on where one is at. Second, there is no separate SSL certificate for the LAN IP address resulting in annoying browser warnings that must be clicked through.
However, presumably due to the fact that traffic through the www.myhost.com style address has to go through the NAT and 192.168.1.x traffic does not, there is a substantial performance difference - transfer rates on the LAN are over 6x faster.
Is there some way to always use the world visible name and yet get LAN performance when on the LAN?
I don't have access to the DNS server in either case, but would something like multicast DNS (aka Bonjour) work?
To make things a bit more complicated, I would also like it to work for a second site. It has a different domain, e.g. www.myhost2.com which replicates the first host. Ideally www.myhost.com to resolve to the IP for www.myhost2.com in the second site's LAN.
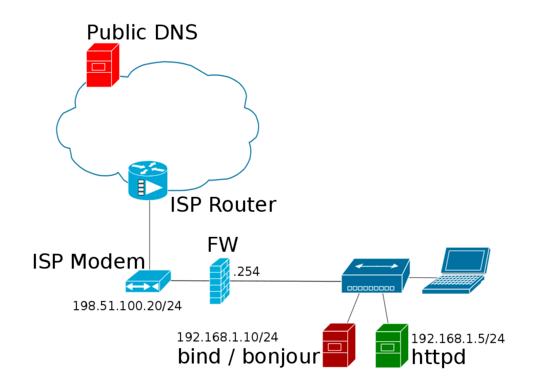
Where is the nameserver for www.myhost.com? If you operate it, what OS is it running? What operating system / webserver are you using? – Mike Pennington – 2014-01-11T23:18:42.680
Are you suggesting a DNS suggestion whereby I make
www.myhost.comresolve to the192.168.1.xaddress on the LAN? – Michael – 2014-01-11T23:20:38.317Yes, that's exactly what I'm suggesting; there are ways to split DNS resolution on a LAN, such that it's different than internet A records – Mike Pennington – 2014-01-11T23:38:59.080
1Mike is suggesting either using different DNS views, or using a split-brain resolver. BTW, unless you're using an antiquated device, performing NAT should have no discernible impact. – Ron Trunk – 2014-01-11T23:58:14.947
@Ron Strangely enough of the two NATs I tested, the newer one has a larger performance difference, but that may be because the LAN is gigabit. – Michael – 2014-01-12T02:25:27.097
@michael What kind of equipment? – Ron Trunk – 2014-01-12T13:08:08.670