5
1
I am trying to set a public SSH key connection from a Windows 7 machine to a Red-Hat Linux machine. The ultimate purpose is to use pscp (PuTTY's version of scp) from the command terminal w/o the need to type password repetitively.
Following PuTTY's documentation and other online sources, I used PuTTYgen to generate a key pair. I then copied the generated public key to a ~/.ssh/authorized_keys file on the Linux machine (as far as I can tell, it runs OpenSSH server).
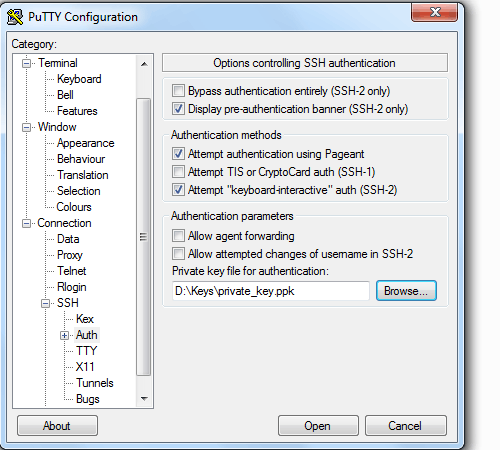
To check the connection, I run PuTTY and set the username and private key file in the appropriate places in its GUI.
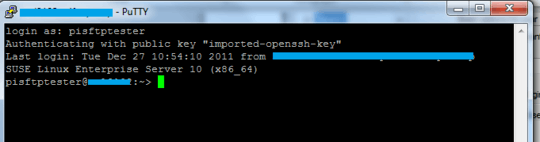
However, when trying to connect using PuTTY's SSH, the connection uses the preset username, but I get an error message of "Server refused our key" and a prompt for the password.
I then tried to copy-paste the public key text from PuTTYgen's GUI to the authorized_keys file, but it did not work either.
How should I set up a public key connection form Win 7 to Linux?
How do I use this with
pscp(rather than PuTTY's ssh)?
Update: Thinking the problem might be with the PuTTYgen key format, I used ssh-keygen on the Linux machine to create an RSA keypair. It generated a id_rsa private key and id_rsa.pub public key. Trying to use > ssh-add id_rsa was not successful, as I git the reply that "Could not open a connection to your authentication agent.", so I just used > cp id_rsa.pub authorized_keys.
I then copied these files to the Windows machine, and used PuTTYgen to convert the private key to a PuTTY private key format (*.ppk). Trying to connect using the new key, I get the response that "Server refused our key".



Did you tried to use python paramiko lib, I do that in job with 600 server at once. – Francisco Tapia – 2015-04-25T13:20:07.750
Make sure the ownership of
~/.sshis correct and that the permissions are0600(+xfor the directory). If you're using SELinux, runningrestorecon -R -v ~/.sshwill make sure that the labels are correct. – Cristian Ciupitu – 2013-11-08T04:08:27.883@CristianCiupitu - I am using Red-Hat. I changed the permissions to
777but it does not solve the problem. – ysap – 2013-11-08T09:34:53.690I didn't say to change the permission to
777(world readable and writable), I said to make them secret. – Cristian Ciupitu – 2013-11-08T13:00:48.427@CristianCiupitu - are you suggesting that '700' and '600' for dir and keys-file are a maximum requirement? SSH should fail because it is world available??? Anyway, I made the change but still no sucess. – ysap – 2013-11-08T14:13:20.647
Check out the logs and update the question. – Cristian Ciupitu – 2013-11-08T18:52:13.990
@CristianCiupitu - What logs? Can you please be more specific? – ysap – 2013-11-08T19:13:49.743
/var/log/secure(and/var/log/messages) probably. – Cristian Ciupitu – 2013-11-08T23:28:22.867@CristianCiupitu - Unfortunately, I don't have access to
/var/log/secure(it has root only permissions). The/var/log/messagesfile contains only a few lines that do not seem to be related to the SSH (looks like it was restarted yesterday, so the log is very short). I viewed it before and after an SSH attempt and there was no change. – ysap – 2013-11-11T14:39:44.690