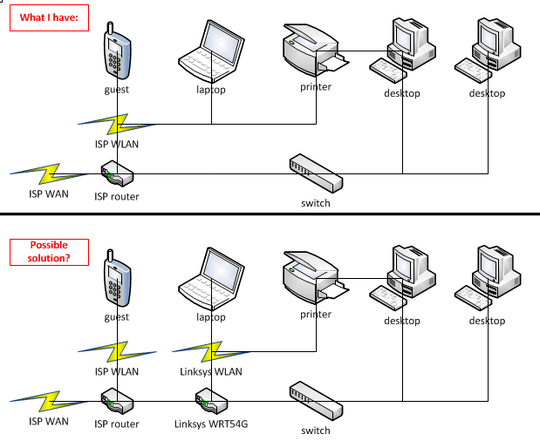
Hook up the Linksys router's WAN port to a LAN port on the ISP-supplied router. Use the Linksys router's provided WLAN for your own use and give guests the credentials for the ISP-supplied router's WLAN.
This puts your own systems behind an additional level of NAT compared to the guest network, which means that your own hosts become to the guests what a normal home network is to the Internet. It also takes advantage of the fact that virtually any such router will consider the WAN side "untrusted". Guests may be able to access the Linksys router (they will certainly likely be able to know that it's there) but not anything behind it, assuming they don't manage to sneak through by directly modifying their local routing tables. (I doubt it'd help them, since they should hit the Linksys's firewall if they try, but it's hard to be 100% certain.)
The major downside to this approach would be that you are giving out the credentials you cannot yourself change. Another potential downside is precisely that it puts yourself behind two layers of NAT, which can conceivably cause problems with any services that rely on the ability to connect back to the originating host (peer-to-peer file sharing springs to mind as one possibility).
You'd end up with something similar to this:
+------------+
| Internet |
+------------+
^
|
+---------+ +------+-----+
| Linksys +--------->| ISP router |
+---------+ +------------+
^ ^
| |
+-----+---------+ +------+--------+
| Your network | | Guest network |
|---------------| |---------------|
| Your host 1 | | Guest host 1 |
| Your host 2 | | Guest host 2 |
+---------------+ +---------------+
The better option would probably be to replace the Linksys with something that supports multiple independent local WLANs, hook that to the ISP-supplied router (configuring the ISP-supplied router for bridge mode if possible), and use only that for local access (your own and guests'), assigning one of its networks for your own use and another for guest use. This is probably a pretty common feature in small-business-range and up hardware, but not so common in consumer hardware. For example, the Cisco RV220W allows you to configure up to four independent wireless networks, each with its own SSID, security settings including encryption and key settings, and network segment isolation settings. That is, you can set things up such that when on one WLAN you can access everything, but if you connect to another, you can only pass through to the WAN, and in particular the guest WLAN cannot access the residence WLAN because the router or access point blocks such communication. I doubt it's bullet proof, but unless your threat model includes targetted attacks from government agencies, I think it would be pretty safe with such a setup (and if that's your threat model, you probably shouldn't have asked here in the first place...).
You'd end up with something like this:
+------------+
| Internet |
+------------+
^
|
+------+-----+
| ISP router |
+------------+
^
|
+------+-----+
+--------->| Your router|<----------+
| +------------+ |
| |
+-------+-------+ +-------+-------+
| Your network | | Guest network |
|---------------| |---------------+
| Your host 1 | | Guest host 1 |
| Your host 2 | | Guest host 2 |
+---------------+ +---------------+
In each diagram, an arrow pointing toward another box means "uses the services of" the pointed-to box. (So e.g. "ISP router" uses the services of "Internet".)
I've done something very similar to the latter case myself with two WLANs on separate VLANs. I don't recall how the router handles the wired network connections, but I'm fairly sure those can also be assigned to chosen VLANs (and such a feature certainly seems reasonable to expect of such a product), which means that you can combine certain wired ports with a given wireless network for your residential network and run a guest network on a VLAN separate from that which you use. If you choose to go this route and the ability to combine and separate traffic on both wired and wireless networks is an important consideration for you, you should probably contact the manufacturers of some products you are considering and ask specifically about that capability.
1Use the Linksys as your protected wlan as the only foreseeable way of making the Linksys handle the guest wlan would be to use a vpn or setup a radius server for your home computers – 50-3 – 2013-09-17T07:07:20.820
If set-up as NAT, your linksys should prevent computers in the guest WLAN to access the home LAN, because you can't route Private-range IP networks. If it doesn, there may be a way to enforce access restrictions in its interface. – mveroone – 2013-09-17T07:28:13.430