11
4
I was confused when I opened my flash drive all I saw was a shortcut with its target as
C:\Windows\system32\rundll32.exe ~$WO.FAT32,_ldr@16 desktop.ini RET TLS " "
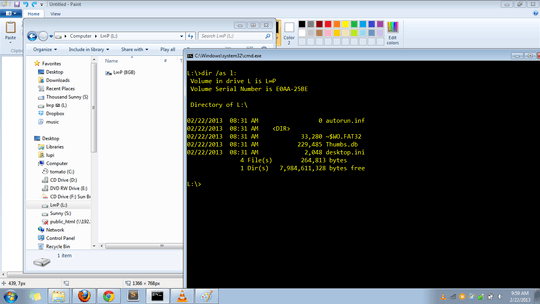
You may refer to the images I uploaded below. It shows the contents of the flash drive. The command prompt shows the hidden contents. You can see there that there is a with a blank name. It contains the contents of the flash drive. That directory also has a desktop.ini inside it with these as contents.
[.ShellClassInfo]
IconResource=%systemroot%\system32\SHELL32.dll,7
IconFile=%SystemRoot%\system32\SHELL32.dll
IconIndex=7
Unlike the first desktop.ini (found at the root of the flash drive). It has some kind of binary contents which frankly I don't know how to paste here. So I just uploaded the contents of the flash drive here. So you can view it yourself.
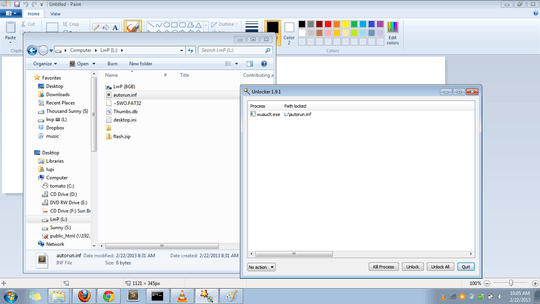
Another weird thing is the autorun.inf (which has only 0 bytes) is being used by the wuauclt.exe. You may refer to the second image below.
Has anyone experienced this too? I already did tried reformatting and reinserting the flash drive but still no luck.
I hashed the desktop.ini (the binary-like one) and searched for it. It pointed me these links which was just posted a few days ago.
http://www.mycity.rs/Ambulanta/problem-sa-memorijskom-karticom-3.html
http://www.mycity.rs/Android/memoriska-kartica_2.html
desktop.ini (binary) d80c46bac5f9df7eb83f46d3f30bf426
I scanned the desktop.ini in VirusTotal. You may see the result here. McAfee-GW-Edition detected it as a Heuristic.BehavesLike.Exploit.CodeExec.C
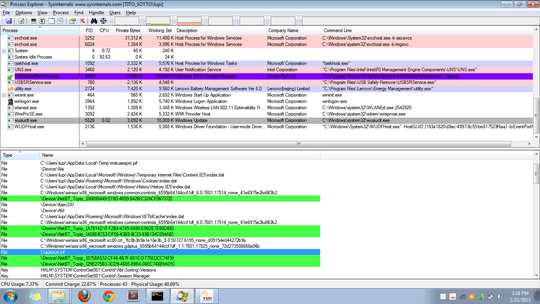
I viewed the handles of wuauclt.exe in the Process Explorer and saw the autorun.inf is being used by the exe. You may also notice that a file from the temp folder is opened.
AppData\Local\Temp\mstuaespm.pif
Here is the scan of that pif file from VirusTotal. Here is an online copy of the PIF file and lastly, a random file that was generated after I ran the PIF file (I used sandbox).
It is turned on and I am using windows. So as far as I know, hidden files in Linux (.foldername) will still be shown in windows. (like the .Trash-0001 folder) – kapitanluffy – 2013-02-22T02:43:42.057
1
Maybe read up on this - http://www.irongeek.com/i.php?page=security/altds
– cutrightjm – 2013-02-22T03:21:48.043If that is the case, won't it be showing in the Explorer like desktop.ini:virus.exe instead of just desktop.ini? (assuming that desktop.ini contains the virus) – kapitanluffy – 2013-02-22T03:27:10.090
If you have read the post, I already uploaded it and provided the link. – kapitanluffy – 2013-02-22T03:33:36.577
start .\test.txt:note.exe did not work in win 7 it says that there is no program associated to perform the requested action. and indicates an access is denied in the command prompt – kapitanluffy – 2013-02-22T03:35:32.660