2
I know routing information is always sent in the clear (oversimplification, but bear with me) so in a scenario where there exists an SSH tunnel between a client and a server using non-standard ports, and the tunnel is encrypted using a secure key exchange with shared secret, is it possible to discern that the traffic itself is SSH? (EG: Is the layer 3 header information in the clear?)
Also, are there other ways to know that this traffic is SSH?
Thanks.
TL;DR: How can you determine an SSH packet is SSH?
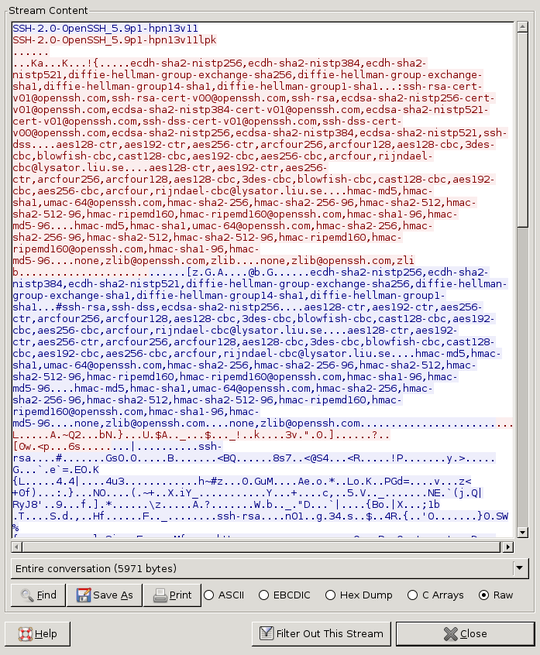
What application is that a screenshot of? – gal – 2012-12-05T04:25:40.330
That is wireshark (http://www.wireshark.org/) - it can capture and/or analyze network traffic
– mulaz – 2012-12-05T10:53:44.123