1
0
I'm trying to setup WAN accessible RDP to a VM on my home LAN to no avail.
I can RDP from inside the LAN just fine, but not outside and I can't seem to debug.
Things I have done/tried:
- Changed Port to 55501 listening and port forwarding
- Tried forwarding public port 55501 to 3389
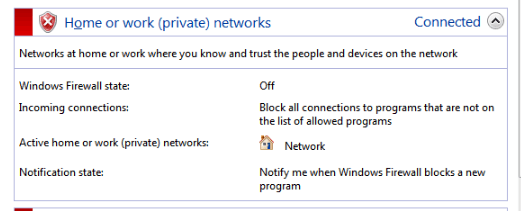
- Disabled Firewall
- Put host in DMZ
- Switched ports back to default (and disabled firewall and put host in DMZ)
I'm at a loss for what else to try and/or how to gather more information as to the issue. Is there a log I can view on the server or guest to see the issue and/or something else I can try?
PS: My Host OS is Windows 10 LTSC the remote guest is Windows 10 Enterprise
Update:
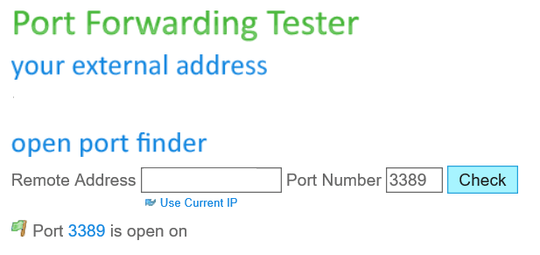
- I am able to see the port open via https://canyouseeme.org/, only when host is in the DMZ, but didn't work with just Port Forwarding.
- My router is a DD-WRT v3 Linksys EA6500
- I looked under Event Viewer and the only thing I could find was "Remote Desktop Server Host role not installed", but googling that came up with Windows Server & DC options, this is not a Domain Joined host and/or a Window Server OS so I wasn't sure how that would apply.
Update2:
- Tried using a fresh install of Windows 10 PRO x64 made via Media Creation Tool and still didn't work, I am reaching the machine as I saw this in Event Viewer
Listener RDP-Tcp received a connection
- Going to try Windows 7 now, see if that fixes it.
Update3 (I'm already being attacked lol, forgot to shut down VM. I will work in securing setup once it works):
Here are my settings, going to try a bounty see if anybody has any solutions...
DMZ:
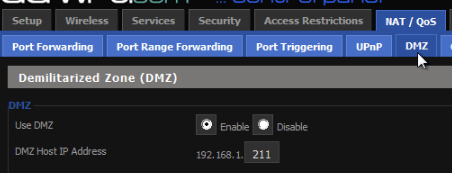 ]
]
Port_Forward:
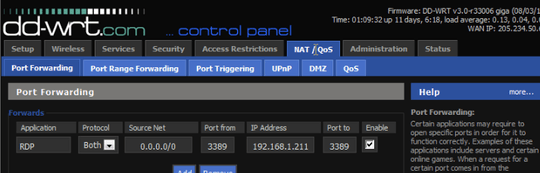
Port Checker:
Windows Firewall:
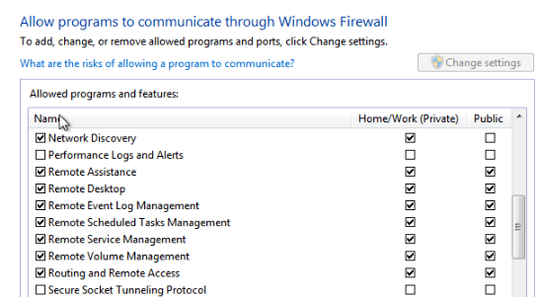
Windows Remote Settings:
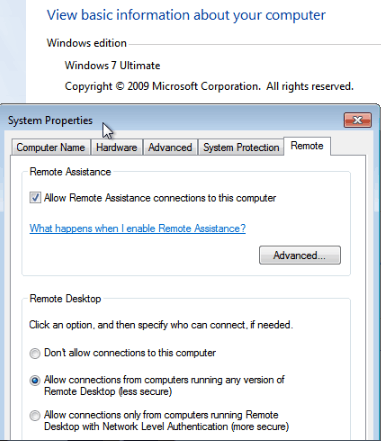
2I would try to scan ports on your router with eg. nmap. Which router/firewall are you using? In Event Viewer, you can find logs under Microsoft -> Windows -> TerminalServices... Please think about using some kind of VPN, RDP does not have a good reputation security-wise. – week – 2019-08-01T13:02:38.137
VPN is not an option as I can't install software on the guest computer, I'm fine with RDP security. I have other ways of protecting my LAN at home, for instance I can power up the VM only when needed remotely. – FreeSoftwareServers – 2019-08-02T07:17:46.297
@week Updated OP in response, tonight I will try setting up a Windows 10 Enterprise RDP server guest which is vanilla. Currently the Windows 10 LTSC VM is quite heavily customized and I wonder if it's somehow related or if the OS itself is to blame, Windows 10 LTSC is not really meant for consumer application, but I love it. – FreeSoftwareServers – 2019-08-02T07:19:08.687
In case there is an open port, some hints of connection in syslog and everything is working within LAN, my bet would be problem with firewall settings on dd-wrt (missing NAT rules or FORWARD rules in/out). – week – 2019-08-02T13:17:57.610
@week Didn't take long for me to start getting attacked! I'm seeing tons of RDP attempts! Opened a bounty, as I'm suspecting your correct the issue might be DD-WRT, but I'm at a loss for what the solution is. – FreeSoftwareServers – 2019-08-06T08:20:57.743
Is IP address
192.168.1.211the host or the VM? – harrymc – 2019-08-06T08:57:59.300That is the VM which I consider the host. I'm trying to connect from what I consider the guest, a remote computer at work running Windows 10 Enterprise. – FreeSoftwareServers – 2019-08-06T10:36:35.217
@harrymc This VM is running on top of KVM not Windows if that's what you were thinking – FreeSoftwareServers – 2019-08-06T13:55:53.563