1
2
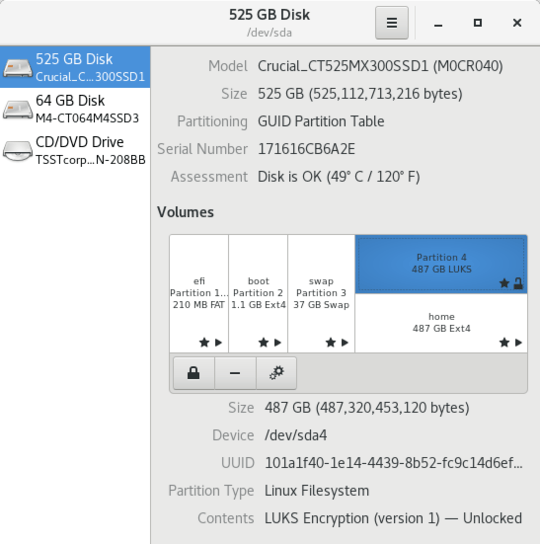
In Linux (Fedora 28) I have my home directory LUKS encryped, when using Gnome Disk (screenshot), I can benchmark separately the underlying LUKS partition (upper blue rectangle) and the decrypted home partition (lower white rectanble).
The LUKS partition gives an access time of 500MB/s, but the decryped acces gives 350MB/s. To be clear this is the same partition a 500GB SSD.
Is it fair to conclude that encryption is slowing down data access by 30% ( = 150/500)?
Is this type of number documented or I am doing some thing wrong. This is much more slowdown that I was expecting.
EDIT: This is my output for
$ cryptsetup benchmark
# Tests are approximate using memory only (no storage IO).
PBKDF2-sha1 384375 iterations per second for 256-bit key
PBKDF2-sha256 494611 iterations per second for 256-bit key
PBKDF2-sha512 323634 iterations per second for 256-bit key
PBKDF2-ripemd160 293225 iterations per second for 256-bit key
PBKDF2-whirlpool 185917 iterations per second for 256-bit key
argon2i 4 iterations, 748334 memory, 4 parallel threads (CPUs) for 256-bit key (requested 2000 ms time)
argon2id 4 iterations, 745443 memory, 4 parallel threads (CPUs) for 256-bit key (requested 2000 ms time)
# Algorithm | Key | Encryption | Decryption
aes-cbc 128b 195.0 MiB/s 664.0 MiB/s
serpent-cbc 128b 28.8 MiB/s 94.7 MiB/s
twofish-cbc 128b 58.8 MiB/s 111.6 MiB/s
aes-cbc 256b 146.5 MiB/s 507.3 MiB/s
serpent-cbc 256b 33.3 MiB/s 110.2 MiB/s
twofish-cbc 256b 59.3 MiB/s 123.6 MiB/s
aes-xts 256b 433.7 MiB/s 416.8 MiB/s
serpent-xts 256b 101.0 MiB/s 94.7 MiB/s
twofish-xts 256b 111.8 MiB/s 110.3 MiB/s
aes-xts 512b 349.5 MiB/s 356.6 MiB/s
serpent-xts 512b 101.6 MiB/s 96.0 MiB/s
twofish-xts 512b 111.2 MiB/s 108.1 MiB/s
$ lscpu | grep aes
Flags: fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge
mca cmov pat pse36 clflush dts acpi mmx fxsr sse sse2 ss ht tm pbe syscall
nx rdtscp lm constant_tsc arch_perfmon pebs bts rep_good nopl xtopology
nonstop_tsc cpuid aperfmperf pni pclmulqdq dtes64 monitor ds_cpl vmx est
tm2 ssse3 cx16 xtpr pdcm pcid sse4_1 sse4_2 x2apic popcnt tsc_deadline_timer
aes xsave avx f16c rdrand lahf_lm cpuid_fault epb pti ssbd ibrs ibpb stibp
tpr_shadow vnmi flexpriority ept vpid fsgsbase smep erms xsaveopt dtherm
ida arat pln pts flush_l1d
NOTE: this question is crossposted here: https://ask.fedoraproject.org/en/question/130463/how-to-activate-the-aes-module-cpu-decryptor/
1Does your CPU support AES-NI or equivalent? Can you check
cryptsetup benchmark? – user1686 – 2018-12-09T23:44:26.7331Yes, it's a fair conclusion. – davidgo – 2018-12-10T00:13:12.283
@grawity, I don't know, how can I find out? do you think there is a better way to tune the disk encryption for a given CPU (mine is Intel® Core™ i7-3612QM CPU @ 2.10GHz × 8 Intel® Ivybridge Mobile). I edited my question with the output of
cryptsetup benchmark. – alfC – 2018-12-10T01:26:41.2631
Run
– user1686 – 2018-12-10T05:51:46.477lscpu | grep aes, additionallylsmod | grep aesand just in casemodinfo aesni_intel. According to Intel ARK it should be supported, but on your benchmark it doesn't show.1
lscpu | grep aesshowsaes(see the edit in my question).lsmod | grep aesshows nothing.modinfo easni_intelgivesmodinfo: ERROR: Module aesni_intel not found.– alfC – 2018-12-10T07:06:02.307