1
I've spent most of my day today trying to figure this out... Not exactly what I had in mind for today... but I couldn't help myself... So, here's the problem: My Windows 7 machine won't authenticate (for a Samba share) to my Ubuntu 18.04 system. I think I've traced this down to the protocol itself, but I'm not sure exactly what the real problem is. It could be a setting I'm missing somewhere in Windows although I've played quite a bit with the NTLM authentication settings in the Local Policy. My Macintosh file share connection to Ubuntu works fine..
So, here's what I've found:
Windows is Resetting the connection from the Ubuntu 18.04 server and restarting the negotiation process with a different port (where my Mac just Acks the STATUS_LOGIN_FAILURE message and continues on it's way).
Windows is sending a different user to the Ubuntu Server (For example
systemname\rootas opposed to my Mac sendingsystemname\\root) (Notice the 2 backslashes instead of 1?)Windows is sending an "Unknown Message Type" to Ubuntu where as my Mac doesn't send anything like this at all.
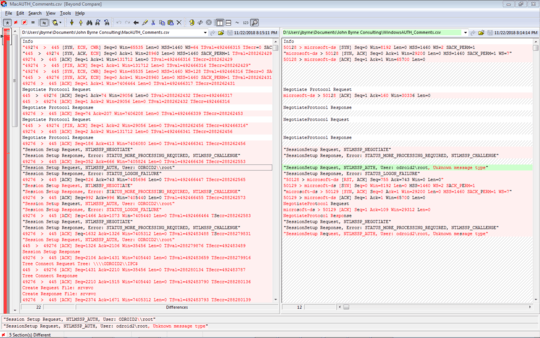
Here's an image of a comparison between the 2 protocols.
I've run into a few sites that may help: https://winprotocoldoc.blob.core.windows.net/productionwindowsarchives/MS-NLMP/[MS-NLMP]-171201.pdf
https://msdn.microsoft.com/en-us/library/cc246324.aspx
I've turned the packet captures from both my Mac and my Windows 7 system into .csv files and put them here for your enjoyment.
Yes, I have looked at the logs (and was 'tail'ing them while trying to connect via file explorer) This is what showed up in the logs:
After a few seconds when the nobody connection times-out (I guess) from just looking at the listing of the computer I get this in the auth.log
Nov 22 21:59:11 odroid2 smbd: pam_unix(samba:session): session closed for user nobody
I also get:
Nov 22 20:08:42 odroid2 smbd: pam_unix(samba:session): session closed for user root
I am authenticating in other ways with 'pam' including with both sshd and smbd:
Nov 22 18:52:34 odroid2 smbd[9524]: pam_unix(samba:session): session opened for user root by (uid=0)
These sessions are from my Mac authenticating. When Windows tries to authenticate, nothing shows in the auth.log other than the nobody if I view the computer (using - net view). I now have net view disabled because NetBIOS was running on port 139 and I wanted it to be the same setup as my Mac (on port 445). So I disabled NetBIOS over TCP/IP.
Nov 22 16:13:56 odroid2 sshd[428]: pam_unix(sshd:session): session opened for user root by (uid=0)
Nov 22 16:13:56 odroid2 systemd-logind[535]: New session 733 of user root.
Nov 22 16:13:57 odroid2 sshd[428]: Received disconnect from 2600:1700:7c20:1fb0:13f:338a:e270:917d port 60469:11: disconnected by user
Nov 22 16:13:57 odroid2 sshd[428]: Disconnected from user root 2600:1700:7c20:1fb0:13f:338a:e270:917d port 60469
Nov 22 16:13:57 odroid2 sshd[428]: pam_unix(sshd:session): session closed for user root
and my syslog doesn't say anything interesting.
Inside my smb.conf I have:
log level = 10
logging = 10
I assumed that 10 was the highest level and that 'all' was the default if nothing was specified. I did see 10 in a sample smb.conf on the internet so that's why I thought it was the highest level.
at https://www.samba.org/samba/docs/current/man-html/smb.conf.5.html
they have:
Example: log level = 3 passdb:5 auth:10 winbind:2
Any help would be greatly appreciated (especially from anyone that works with Microsoft and knows these protocols and what they should look like)
Windows Packet Capture (Just the SMB and related TCP/IP packets)
No.,Time,Source,Destination,Protocol,Info
13,1.627011,10.100.1.66,10.100.1.99,TCP,50128 > microsoft-ds [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=2 SACK_PERM=1
14,1.627457,10.100.1.99,10.100.1.66,TCP,"microsoft-ds > 50128 [SYN, ACK] Seq=0 Ack=1 Win=29200 Len=0 MSS=1460 SACK_PERM=1 WS=7"
15,1.627639,10.100.1.66,10.100.1.99,TCP,50128 > microsoft-ds [ACK] Seq=1 Ack=1 Win=65700 Len=0
16,1.627723,10.100.1.66,10.100.1.99,SMB,Negotiate Protocol Request
17,1.628079,10.100.1.99,10.100.1.66,TCP,microsoft-ds > 50128 [ACK] Seq=1 Ack=160 Win=30336 Len=0
18,1.646459,10.100.1.99,10.100.1.66,SMB2,NegotiateProtocol Response
19,1.646607,10.100.1.66,10.100.1.99,SMB2,NegotiateProtocol Request
20,1.64793,10.100.1.99,10.100.1.66,SMB2,NegotiateProtocol Response
21,1.648412,10.100.1.66,10.100.1.99,SMB2,"SessionSetup Request, NTLMSSP_NEGOTIATE"
22,1.651446,10.100.1.99,10.100.1.66,SMB2,"SessionSetup Response, Error: STATUS_MORE_PROCESSING_REQUIRED, NTLMSSP_CHALLENGE"
23,1.651682,10.100.1.66,10.100.1.99,SMB2,"SessionSetup Request, NTLMSSP_AUTH, User: SMBServerSystem\root, Unknown message type"
24,1.658833,10.100.1.99,10.100.1.66,SMB2,"SessionSetup Response, Error: STATUS_LOGON_FAILURE"
25,1.658923,10.100.1.66,10.100.1.99,TCP,"50128 > microsoft-ds [RST, ACK] Seq=755 Ack=743 Win=0 Len=0"
100,6.881635,10.100.1.66,10.100.1.99,TCP,50129 > microsoft-ds [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=2 SACK_PERM=1
101,6.88205,10.100.1.99,10.100.1.66,TCP,"microsoft-ds > 50129 [SYN, ACK] Seq=0 Ack=1 Win=29200 Len=0 MSS=1460 SACK_PERM=1 WS=7"
102,6.882208,10.100.1.66,10.100.1.99,TCP,50129 > microsoft-ds [ACK] Seq=1 Ack=1 Win=65700 Len=0
103,6.882313,10.100.1.66,10.100.1.99,SMB2,NegotiateProtocol Request
104,6.882666,10.100.1.99,10.100.1.66,TCP,microsoft-ds > 50129 [ACK] Seq=1 Ack=109 Win=29312 Len=0
105,6.900185,10.100.1.99,10.100.1.66,SMB2,NegotiateProtocol Response
106,6.900746,10.100.1.66,10.100.1.99,SMB2,"SessionSetup Request, NTLMSSP_NEGOTIATE"
107,6.90437,10.100.1.99,10.100.1.66,SMB2,"SessionSetup Response, Error: STATUS_MORE_PROCESSING_REQUIRED, NTLMSSP_CHALLENGE"
108,6.9046,10.100.1.66,10.100.1.99,SMB2,"SessionSetup Request, NTLMSSP_AUTH, User: SMBServerSystem\root, Unknown message type"
109,6.911834,10.100.1.99,10.100.1.66,SMB2,"SessionSetup Response, Error: STATUS_LOGON_FAILURE"
110,6.91193,10.100.1.66,10.100.1.99,TCP,"50129 > microsoft-ds [RST, ACK] Seq=596 Ack=537 Win=0 Len=0"
Packet capture of my Mac (SMB&TCP/IP Packets)
No.,Time,Source,Destination,Protocol,Length,Info
2774,8.760436,Mac-ClientSMB.local,SMBServerHostname.local,TCP,78,"49274 > 445 [SYN, ECN, CWR] Seq=0 Win=65535 Len=0 MSS=1460 WS=64 TSval=492466315 TSecr=0 SACK_PERM=1"
2776,8.761635,SMBServerHostname.local,Mac-ClientSMB.local,TCP,74,"445 > 49274 [SYN, ACK, ECN] Seq=0 Ack=1 Win=28960 Len=0 MSS=1460 SACK_PERM=1 TSval=288262429 TSecr=492466315 WS=128"
2777,8.761677,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49274 > 445 [ACK] Seq=1 Ack=1 Win=131712 Len=0 TSval=492466316 TSecr=288262429
2778,8.761725,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,"49274 > 445 [FIN, ACK] Seq=1 Ack=1 Win=131712 Len=0 TSval=492466316 TSecr=288262429"
2781,8.761973,Mac-ClientSMB.local,SMBServerHostname.local,TCP,78,"49276 > 445 [SYN, ECN, CWR] Seq=0 Win=65535 Len=0 MSS=1460 WS=128 TSval=492466316 TSecr=0 SACK_PERM=1"
2782,8.763016,SMBServerHostname.local,Mac-ClientSMB.local,TCP,74,"445 > 49276 [SYN, ACK, ECN] Seq=0 Ack=1 Win=28960 Len=0 MSS=1460 SACK_PERM=1 TSval=288262431 TSecr=492466316 WS=128"
2783,8.763048,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=1 Ack=1 Win=7406464 Len=0 TSval=492466317 TSecr=288262431
2784,8.763082,Mac-ClientSMB.local,SMBServerHostname.local,SMB,139,Negotiate Protocol Request
2785,8.764474,SMBServerHostname.local,Mac-ClientSMB.local,TCP,66,445 > 49276 [ACK] Seq=1 Ack=74 Win=29056 Len=0 TSval=288262432 TSecr=492466317
2786,8.764477,SMBServerHostname.local,Mac-ClientSMB.local,TCP,66,445 > 49274 [ACK] Seq=1 Ack=2 Win=29056 Len=0 TSval=288262432 TSecr=492466316
2790,8.786105,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,272,Negotiate Protocol Response
2791,8.786172,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=74 Ack=207 Win=7406208 Len=0 TSval=492466339 TSecr=288262453
2792,8.786222,Mac-ClientSMB.local,SMBServerHostname.local,SMB2,178,Negotiate Protocol Request
2793,8.788306,SMBServerHostname.local,Mac-ClientSMB.local,TCP,66,"445 > 49274 [FIN, ACK] Seq=1 Ack=2 Win=29056 Len=0 TSval=288262456 TSecr=492466316"
2794,8.788355,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49274 > 445 [ACK] Seq=2 Ack=2 Win=131712 Len=0 TSval=492466341 TSecr=288262456
2795,8.788573,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,272,Negotiate Protocol Response
2796,8.788611,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=186 Ack=413 Win=7406080 Len=0 TSval=492466341 TSecr=288262456
2800,8.881565,Mac-ClientSMB.local,SMBServerHostname.local,SMB2,232,"Session Setup Request, NTLMSSP_NEGOTIATE"
2801,8.885411,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,319,"Session Setup Response, Error: STATUS_MORE_PROCESSING_REQUIRED, NTLMSSP_CHALLENGE"
2802,8.885488,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=352 Ack=666 Win=7405824 Len=0 TSval=492466436 TSecr=288262553
2803,8.887756,Mac-ClientSMB.local,SMBServerHostname.local,SMB2,540,"Session Setup Request, NTLMSSP_AUTH, User: SMBServerHostname\\root"
2804,8.896983,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,143,"Session Setup Response, Error: STATUS_LOGON_FAILURE"
2805,8.897079,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=826 Ack=743 Win=7405696 Len=0 TSval=492466447 TSecr=288262565
2806,8.902278,Mac-ClientSMB.local,SMBServerHostname.local,SMB2,232,"Session Setup Request, NTLMSSP_NEGOTIATE"
2807,8.905787,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,319,"Session Setup Response, Error: STATUS_MORE_PROCESSING_REQUIRED, NTLMSSP_CHALLENGE"
2808,8.905878,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=992 Ack=996 Win=7405440 Len=0 TSval=492466455 TSecr=288262573
2809,8.907242,Mac-ClientSMB.local,SMBServerHostname.local,SMB2,540,"Session Setup Request, NTLMSSP_AUTH, User: SMBServerHostname\\root"
2810,8.915419,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,143,"Session Setup Response, Error: STATUS_LOGON_FAILURE"
2811,8.915507,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=1466 Ack=1073 Win=7405440 Len=0 TSval=492466464 TSecr=288262583
3769,26.062858,Mac-ClientSMB.local,SMBServerHostname.local,SMB2,232,"Session Setup Request, NTLMSSP_NEGOTIATE"
3770,26.163475,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,319,"Session Setup Response, Error: STATUS_MORE_PROCESSING_REQUIRED, NTLMSSP_CHALLENGE"
3771,26.163543,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=1632 Ack=1326 Win=7405312 Len=0 TSval=492483488 TSecr=288279831
3772,26.165485,Mac-ClientSMB.local,SMBServerHostname.local,SMB2,540,"Session Setup Request, NTLMSSP_AUTH, User: SMBServerHostname\\root"
3773,26.336004,SMBServerHostname.local,Mac-ClientSMB.local,TCP,66,445 > 49276 [ACK] Seq=1326 Ack=2106 Win=35456 Len=0 TSval=288279876 TSecr=492483489
3775,26.336007,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,171,Session Setup Response
3776,26.336087,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=2106 Ack=1431 Win=7405440 Len=0 TSval=492483659 TSecr=288279916
3783,26.46547,Mac-ClientSMB.local,SMBServerHostname.local,SMB2,170,Tree Connect Request Tree: \\\\SMBServerHostname\\IPC$
3784,26.466583,SMBServerHostname.local,Mac-ClientSMB.local,TCP,66,445 > 49276 [ACK] Seq=1431 Ack=2210 Win=35456 Len=0 TSval=288280134 TSecr=492483787
3785,26.46866,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,150,Tree Connect Response
3786,26.468706,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=2210 Ack=1515 Win=7405440 Len=0 TSval=492483790 TSecr=288280136
3787,26.468819,Mac-ClientSMB.local,SMBServerHostname.local,SMB2,230,Create Request File: srvsvc
3788,26.471771,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,222,Create Response File: srvsvc
3789,26.471838,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=2374 Ack=1671 Win=7405312 Len=0 TSval=492483793 TSecr=288280139
3790,26.47217,Mac-ClientSMB.local,SMBServerHostname.local,DCERPC,262,"Bind: call_id: 1, Fragment: Single, 1 context items: SRVSVC V3.0 (32bit NDR)"
3791,26.474815,SMBServerHostname.local,Mac-ClientSMB.local,DCERPC,250,"Bind_ack: call_id: 1, Fragment: Single, max_xmit: 4280 max_recv: 4280, 1 results: Acceptance"
3792,26.474859,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=2570 Ack=1855 Win=7405312 Len=0 TSval=492483796 TSecr=288280142
3793,26.475701,Mac-ClientSMB.local,SMBServerHostname.local,SRVSVC,278,NetShareEnumAll request
3794,26.479409,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,143,"Ioctl Response, Error: STATUS_PENDING"
3795,26.47947,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=2782 Ack=1932 Win=7405440 Len=0 TSval=492483800 TSecr=288280147
3796,26.479634,SMBServerHostname.local,Mac-ClientSMB.local,SRVSVC,702,NetShareEnumAll response
3797,26.479689,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=2782 Ack=2568 Win=7404928 Len=0 TSval=492483800 TSecr=288280147
3798,26.480282,Mac-ClientSMB.local,SMBServerHostname.local,SMB2,158,Close Request File: srvsvc
3799,26.481727,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,194,Close Response
3800,26.48178,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=2874 Ack=2696 Win=7405440 Len=0 TSval=492483802 TSecr=288280149
3801,26.48186,Mac-ClientSMB.local,SMBServerHostname.local,SMB2,138,Tree Disconnect Request
3802,26.483827,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,138,Tree Disconnect Response
3803,26.483897,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=2946 Ack=2768 Win=7405440 Len=0 TSval=492483804 TSecr=288280151
3824,28.16751,Mac-ClientSMB.local,SMBServerHostname.local,SMB2,182,Tree Connect Request Tree: \\\\SMBServerHostname\\SMBServerHostnameLOGS
3829,28.242395,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,150,Tree Connect Response
3830,28.24248,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=3062 Ack=2852 Win=7405440 Len=0 TSval=492485552 TSecr=288281910
3834,28.245251,Mac-ClientSMB.local,SMBServerHostname.local,SMB2,170,Tree Connect Request Tree: \\\\SMBServerHostname\\IPC$
3835,28.248006,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,150,Tree Connect Response
3836,28.248048,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=3166 Ack=2936 Win=7405440 Len=0 TSval=492485556 TSecr=288281915
3837,28.248134,Mac-ClientSMB.local,SMBServerHostname.local,SMB2,230,Create Request File: lsarpc
3838,28.250815,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,222,Create Response File: lsarpc
3839,28.250856,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=3330 Ack=3092 Win=7405312 Len=0 TSval=492485558 TSecr=288281918
3840,28.251021,Mac-ClientSMB.local,SMBServerHostname.local,DCERPC,262,"Bind: call_id: 3, Fragment: Single, 1 context items: LSARPC V0.0 (32bit NDR)"
3841,28.253495,SMBServerHostname.local,Mac-ClientSMB.local,DCERPC,250,"Bind_ack: call_id: 3, Fragment: Single, max_xmit: 4280 max_recv: 4280, 1 results: Acceptance"
3842,28.253538,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=3526 Ack=3276 Win=7405312 Len=0 TSval=492485560 TSecr=288281921
3843,28.253699,Mac-ClientSMB.local,SMBServerHostname.local,LSARPC,258,lsa_GetUserName request
3844,28.256607,SMBServerHostname.local,Mac-ClientSMB.local,LSARPC,286,lsa_GetUserName response
3845,28.256683,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=3718 Ack=3496 Win=7405312 Len=0 TSval=492485563 TSecr=288281924
3846,28.256923,Mac-ClientSMB.local,SMBServerHostname.local,LSARPC,282,lsa_OpenPolicy2 request
3847,28.259367,SMBServerHostname.local,Mac-ClientSMB.local,LSARPC,230,lsa_OpenPolicy2 response
3848,28.259444,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=3934 Ack=3660 Win=7405312 Len=0 TSval=492485565 TSecr=288281926
3849,28.259879,Mac-ClientSMB.local,SMBServerHostname.local,LSARPC,302,lsa_LookupNames request
3850,28.263534,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,143,"Ioctl Response, Error: STATUS_PENDING"
3851,28.263539,SMBServerHostname.local,Mac-ClientSMB.local,LSARPC,326,lsa_LookupNames response
3852,28.263647,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=4170 Ack=3737 Win=7405440 Len=0 TSval=492485569 TSecr=288281931
3853,28.263647,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=4170 Ack=3997 Win=7405184 Len=0 TSval=492485569 TSecr=288281931
3854,28.263903,Mac-ClientSMB.local,SMBServerHostname.local,LSARPC,234,lsa_Close request
3855,28.266342,SMBServerHostname.local,Mac-ClientSMB.local,LSARPC,230,lsa_Close response
3856,28.266439,Mac-ClientSMB.local,SMBServerHostname.local,TCP,66,49276 > 445 [ACK] Seq=4338 Ack=4161 Win=7405312 Len=0 TSval=492485571 TSecr=288281933
3857,28.266709,Mac-ClientSMB.local,SMBServerHostname.local,SMB2,158,Close Request File: lsarpc
3858,28.267637,Mac-ClientSMB.local,SMBServerHostname.local,SMB2,222,Ioctl Request FSCTL_VALIDATE_NEGOTIATE_INFO
3859,28.268592,SMBServerHostname.local,Mac-ClientSMB.local,SMB2,194,Close Response
If you really need them... here are the actual pcap/pcapng files... Once this is solved... I'm taking them down because there's personal information in them and anyone who wants to view the answer will have to do so without the actual pcap data.
links:
https://drive.google.com/open?id=1AtPJ_t2CUt1NxQz84pu7xu7UMtnjvgc3
https://drive.google.com/open?id=1HO9UtQ8a5idvfsHdL6gmsUqvW6YCDFCP
I would almost bet that the backslash differences are an artifact of the capture tool's CSV exporting, and not actually sent on the wire. Can you attach the actual pcap files instead? And, have you tried checking the server's Samba logs yet? (Use
[global] log level = 1 passdb:5 auth:5 auth_audit:5.) – user1686 – 2018-11-23T07:21:24.510I just put the actual pcap files (saved with the SMB2 marked packets) up. Thanks for taking a look at this. – John Byrne – 2018-11-23T08:03:28.747