3
I have my RaspberryPi3 (latest Raspbian) connected via WiFi to my WLAN router
with ip=192.168.1.1 and mac=XX:XX:XX:XX:XX:A5. However, when I perform
the following, I get quite different results for the MAC.
# ifconfig wlan0
wlan0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.1.198 netmask 255.255.255.0 broadcast 192.168.1.255
...
ether ZZ:ZZ:ZZ:ZZ:ZZ:c9 txqueuelen 1000 (Ethernet)
...
# arp -ni wlan0
Address HWtype HWaddress Flags Mask Iface
192.168.1.1 ether XX:XX:XX:XX:XX:A5 C wlan0
# iw wlan0 info
Interface wlan0
...
addr ZZ:ZZ:ZZ:ZZ:ZZ:c9
# iw wlan0 link
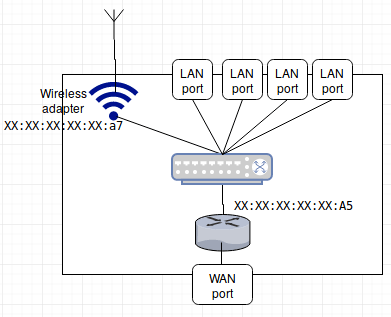
Connected to XX:XX:XX:XX:XX:a7 (on wlan0)
...
# iwconfig wlan0
...
Mode:Managed Frequency:2.412 GHz Access Point: XX:XX:XX:XX:XX:a7
# iw --version
iw version 4.9
The iw man pages, doesn't say much.
- As for
ifconfig, it shows my own adapter MAC (ZZ:ZZ:ZZ:ZZ:ZZ:c9). - As for
arp, it shows the correct WLAN router MAC (XX:XX:XX:XX:XX:A5). - But for
iw wlan link, it shows a third MAC! (XX:XX:XX:XX:XX:a7)! - And for
iwconfig wlan0, it also show that 3rd MAC.
Q. What is that mysterious 3rd MAC address representing?
UPDATE
Thanks to the info provided by @mtak we need to look at what is going on in the different OSI layers. Most IP discovery operations take place on the Network Layer (L3), whereas the MAC "stuff" happen on the Data Link layer (L2) and below (Physical).
Perhaps that's the Access Point's MAC address as per "
– Pimp Juice IT – 2018-01-03T11:58:17.593Access Point: ~" and "Connected to ~".... " iwconfig will display the name of the MAC protocol used " .... So the MAC address of the Wi-Fi Access Point endpoint you connect to for accessing that network via Wi-Fi.It can't be because the AP is the one with
:A5. I've checked this with bothnmapand from other machines on the local network. The only other thing I can think of is that the wifi of an RPi3 can also act as a repeater. So perhaps iwconfig is reading the MAC of a would-be-ap or is simply buggy? – not2qubit – 2018-01-03T13:35:16.143