3
Since last several days, task manager shows 200-300Kbps (with small b) receive networking at idle time without opening any application. Though I block all apps in firewall (except system PID 4), task manager shows same network activity. When I open Wireshark to check network packets it shows some weired network activity. Even this ether type 0x880a and 0x5524 is not documented in IEEE 802 Numbers. Also that MAC address doesn't belong to any host of my Ethernet IPv4 subnetwork (/25). Here is the packet's metadata & data in plain text.
Source Destination Protocol Length Sender IP address Info
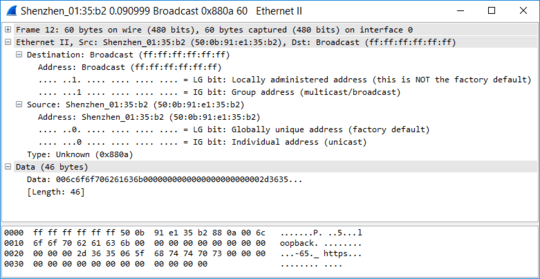
Shenzhen_01:35:b2 Broadcast 0x880a 60 Ethernet II
Ethernet II, Src: Shenzhen_01:35:b2 (50:0b:91:e1:35:b2), Dst: Broadcast (ff:ff:ff:ff:ff:ff)
Data (46 bytes)
0000 00 6c 6f 6f 70 62 61 63 6b 00 00 00 00 00 00 00 .loopback.......
0010 00 00 00 00 00 2d 36 35 06 5f 68 74 74 70 73 00 .....-65._https.
0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ..............
Data: 006c6f6f706261636b0000000000000000000000002d3635...
[Length: 46]
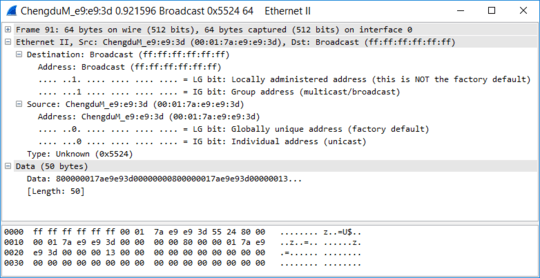
Source Destination Protocol Length Sender IP address Type Info
ChengduM_e9:e9:3d Broadcast 0x5524 64 0x5524 Ethernet II
Ethernet II, Src: ChengduM_e9:e9:3d (00:01:7a:e9:e9:3d), Dst: Broadcast (ff:ff:ff:ff:ff:ff)
Data (50 bytes)
0000 80 00 00 01 7a e9 e9 3d 00 00 00 00 80 00 00 01 ....z..=........
0010 7a e9 e9 3d 00 00 00 13 00 00 00 00 00 00 00 00 z..=............
0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0030 00 00 ..
Data: 800000017ae9e93d00000000800000017ae9e93d00000013...
[Length: 50]
- Question: What are these unknown Ethernet packets? Are those malicious? Is ISP networking responsible for these network packets?
If you don't get answers here, also try https://reverseengineering.stackexchange.com/
– dirkt – 2017-12-19T17:46:49.217Note that the main registry of ethertypes is maintained by IEEE – not that it helps much, as 0x880A is merely part of the "reserved for 802.3 Ethernet" range. Also, since it doesn't carry IP, your IPv4 subnetwork is quite irrelevant.
– user1686 – 2017-12-19T17:48:46.007@dirkt I did not relate this problem with Reverse engineering. I'm afraid of MITM. – Biswapriyo – 2017-12-19T17:49:31.040
Keep unplugging stuff until you find the source. (It might be a Wi-Fi connected device.) – user1686 – 2017-12-19T17:50:20.733
@grawity No WiFi, no other devices connected to Ethernet, just my PC. – Biswapriyo – 2017-12-19T17:52:58.493