2
I want to configure my home network in a more "secure" way and can't seems to find any obvious way to do it, despite it seems to me a pretty common need.
The idea is that I don't want some of the wired and wireless devices connected to be able to communicate with to any other devices of the network. I only want them to have internet access. I will call theses devices "toxic" devices. I don't want to make difference if the device is connected using WiFi or wire, they may be "toxic" or not.
Here are the "optional" requirement but I would very much like theses to apply:
- Avoid as much as possible to duplicate hardware or wire only to separate the "toxic" of the non-toxic.
- If all this could be "soft-configured" which device is toxic or not, and be able to switch the device from toxic to non-toxic, without the need to manually change the underlying wires
- Toxic devices wouldn't be able to communicate to each other (But I could tolerate that theses are all in the same subnet)
- For performance reasons, keep only 1 WiFi device activated per Frequency range(ex. 1 x 2.4Ghz + 1 x 5Ghz)... (Doesn't 2 WiFi device next to each other have to split the bandwith ??)
Here is my hardware:
- LinkSys BEFSX41 (old stuff, Wire Only router)
- Cisco Linksys EA3500 (2.4Ghz, 5Ghz)
- A ISP (Bell) custom router (2.4Ghz). The WAN port can't be used because it seems hardcoded to a specific Gateway. Actually used as a WiFi Access Point only.
- (I also have a switch, but I don't think it is relevant here)
- I would be willing to invest more money in some hardware (about 300$ max)
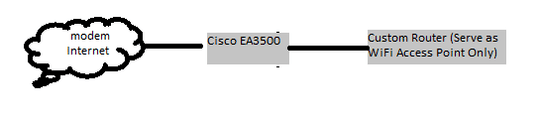
My actual Setup:
- LinkSys BEFSX41 not used.
- LinkSys EA3500: All WiFi is disabled.
- Custom router used as an WiFi Access Point.
- Every one have access to everything behind my Firewall.
Image:
I do not expect anyone to "hack" my network. I just want to avoid broad spectrum viruses to infect my network's computers/devices – NoNameStackExchange – 2017-10-16T00:30:31.780